Tutorial
How To Install Nagios 4 and Monitor Your Servers on Ubuntu 14.04

Not using Ubuntu 14.04?Choose a different version or distribution.
Introduction
In this tutorial, we will cover the installation of Nagios 4, a very popular open source monitoring system, on Ubuntu 14.04. We will cover some basic configuration, so you will be able to monitor host resources via the web interface. We will also utilize the Nagios Remote Plugin Executor (NRPE), that will be installed as an agent on remote hosts, to monitor their local resources.
Nagios is useful for keeping an inventory of your servers, and making sure your critical services are up and running. Using a monitoring system, like Nagios, is an essential tool for any production server environment.
Prerequisites
To follow this tutorial, you must have superuser privileges on the Ubuntu 14.04 server that will run Nagios. Ideally, you will be using a non-root user with superuser privileges. If you need help setting that up, follow the steps 1 through 3 in this tutorial: Initial Server Setup with Ubuntu 14.04.
A LAMP stack is also required. Follow this tutorial if you need to set that up: How To Install Linux, Apache, MySQL, PHP (LAMP) stack on Ubuntu 14.04.
This tutorial assumes that your server has private networking enabled. If it doesn’t, just replace all the references to private IP addresses with public IP addresses.
Now that we have the prerequisites sorted out, let’s move on to getting Nagios 4 installed.
Install Nagios 4
This section will cover how to install Nagios 4 on your monitoring server. You only need to complete this section once.
Create Nagios User and Group
We must create a user and group that will run the Nagios process. Create a “nagios” user and “nagcmd” group, then add the user to the group with these commands:
Install Build Dependencies
Because we are building Nagios Core from source, we must install a few development libraries that will allow us to complete the build. While we’re at it, we will also install apache2-utils, which will be used to set up the Nagios web interface.
First, update your apt-get package lists:
Then install the required packages:
Let’s install Nagios now.
Install Nagios Core
Download the source code for the latest stable release of Nagios Core. Go to the Nagios downloads page, and click the Skip to download link below the form. Copy the link address for the latest stable release so you can download it to your Nagios server.
At the time of this writing, the latest stable release is Nagios 4.1.1. Download it to your home directory with curl:
cd ~
curl -L -O https://assets.nagios.com/downloads/nagioscore/releases/nagios-4.1.1.tar.gz
Extract the Nagios archive with this command:
Then change to the extracted directory:
Before building Nagios, we must configure it. If you want to configure it to use postfix (which you can install with apt-get), add --with-mail=/usr/sbin/sendmail to the following command:
Now compile Nagios with this command:
Now we can run these make commands to install Nagios, init scripts, and sample configuration files:
In order to issue external commands via the web interface to Nagios, we must add the web server user, www-data, to the nagcmd group:
Install Nagios Plugins
Find the latest release of Nagios Plugins here: Nagios Plugins Download. Copy the link address for the latest version, and copy the link address so you can download it to your Nagios server.
At the time of this writing, the latest version is Nagios Plugins 2.1.1. Download it to your home directory with curl:
cd ~
curl -L -O http://nagios-plugins.org/download/nagios-plugins-2.1.1.tar.gz
Extract Nagios Plugins archive with this command:
Then change to the extracted directory:
Before building Nagios Plugins, we must configure it. Use this command:
Now compile Nagios Plugins with this command:
Then install it with this command:
Install NRPE
Find the source code for the latest stable release of NRPE at the NRPE downloads page. Download the latest version to your Nagios server.
At the time of this writing, the latest release is 2.15. Download it to your home directory with curl:
Extract the NRPE archive with this command:
Then change to the extracted directory:
Configure NRPE with these commands:
Now build and install NRPE and its xinetd startup script with these commands:
Open the xinetd startup script in an editor:
Modify the only_from line by adding the private IP address of the your Nagios server to the end (substitute in the actual IP address of your server):
only_from = 127.0.0.1 10.132.224.168
Save and exit. Only the Nagios server will be allowed to communicate with NRPE.
Restart the xinetd service to start NRPE:
Now that Nagios 4 is installed, we need to configure it.
Configure Nagios
Now let’s perform the initial Nagios configuration. You only need to perform this section once, on your Nagios server.
Organize Nagios Configuration
Open the main Nagios configuration file in your favorite text editor. We’ll use vi to edit the file:
sudo vi /usr/local/nagios/etc/nagios.cfg
Now find an uncomment this line by deleting the #:
#cfg_dir=/usr/local/nagios/etc/servers
Save and exit.
Now create the directory that will store the configuration file for each server that you will monitor:
sudo mkdir /usr/local/nagios/etc/servers
Configure Nagios Contacts
Open the Nagios contacts configuration in your favorite text editor. We’ll use vi to edit the file:
sudo vi /usr/local/nagios/etc/objects/contacts.cfg
Find the email directive, and replace its value (the highlighted part) with your own email address:
email nagios@localhost ; <<***** CHANGE THIS TO YOUR EMAIL ADDRESS ******
Save and exit.
Configure check_nrpe Command
Let’s add a new command to our Nagios configuration:
Add the following to the end of the file:
define command{
command_name check_nrpe
command_line $USER1$/check_nrpe -H $HOSTADDRESS$ -c $ARG1$
}
Save and exit. This allows you to use the check_nrpe command in your Nagios service definitions.
Configure Apache
Enable the Apache rewrite and cgi modules:
sudo a2enmod rewrite
sudo a2enmod cgi
Use htpasswd to create an admin user, called “nagiosadmin”, that can access the Nagios web interface:
sudo htpasswd -c /usr/local/nagios/etc/htpasswd.users nagiosadmin
Enter a password at the prompt. Remember this password, as you will need it to access the Nagios web interface.
Note: If you create a user that is not named “nagiosadmin”, you will need to edit /usr/local/nagios/etc/cgi.cfg and change all the “nagiosadmin” references to the user you created.
Now create a symbolic link of nagios.conf to the sites-enabled directory:
sudo ln -s /etc/apache2/sites-available/nagios.conf /etc/apache2/sites-enabled/
Nagios is ready to be started. Let’s do that, and restart Apache:
sudo service nagios start
sudo service apache2 restart
To enable Nagios to start on server boot, run this command:
sudo ln -s /etc/init.d/nagios /etc/rcS.d/S99nagios
Optional: Restrict Access by IP Address
If you want to restrict the IP addresses that can access the Nagios web interface, you will want to edit the Apache configuration file:
sudo vi /etc/apache2/sites-available/nagios.conf
Find and comment the following two lines by adding # symbols in front of them:
Order allow,deny
Allow from all
Then uncomment the following lines, by deleting the # symbols, and add the IP addresses or ranges (space delimited) that you want to allow to in the Allow from line:
# Order deny,allow
# Deny from all
# Allow from 127.0.0.1
As these lines will appear twice in the configuration file, so you will need to perform these steps once more.
Save and exit.
Now restart Apache to put the change into effect:
sudo service nagios restart
sudo service apache2 restart
Nagios is now running, so let’s try and log in.
Accessing the Nagios Web Interface
Open your favorite web browser, and go to your Nagios server (substitute the IP address or hostname for the highlighted part):
http://nagios_server_public_ip/nagios
Because we configured Apache to use htpasswd, you must enter the login credentials that you created earlier. We used “nagiosadmin” as the username:
After authenticating, you will be see the default Nagios home page. Click on the Hosts link, in the left navigation bar, to see which hosts Nagios is monitoring:
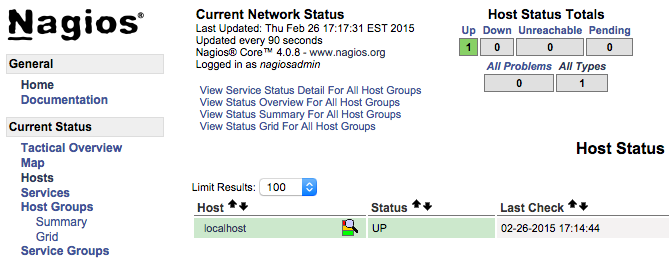
As you can see, Nagios is monitoring only “localhost”, or itself.
Let’s monitor another host with Nagios!
Monitor a Host with NRPE
In this section, we’ll show you how to add a new host to Nagios, so it will be monitored. Repeat this section for each server you wish to monitor.
On a server that you want to monitor, update apt-get:
sudo apt-get update
Now install Nagios Plugins and NRPE:
sudo apt-get install nagios-plugins nagios-nrpe-server
Configure Allowed Hosts
Now, let’s update the NRPE configuration file. Open it in your favorite editor (we’re using vi):
sudo vi /etc/nagios/nrpe.cfg
Find the allowed_hosts directive, and add the private IP address of your Nagios server to the comma-delimited list (substitute it in place of the highlighted example):
allowed_hosts=127.0.0.1,10.132.224.168
Save and exit. This configures NRPE to accept requests from your Nagios server, via its private IP address.
Configure Allowed NRPE Commands
Look up the name of your root filesystem (because it is one of the items we want to monitor):
df -h /
We will be using the filesystem name in the NRPE configuration to monitor your disk usage (it is probably /dev/vda). Now open nrpe.cfg for editing:
sudo vi /etc/nagios/nrpe.cfg
The NRPE configuration file is very long and full of comments. There are a few lines that you will need to find and modify:
- server_address: Set to the private IP address of this host
- allowed_hosts: Set to the private IP address of your Nagios server
- command[check_hda1]: Change
/dev/hda1to whatever your root filesystem is called
The three aforementioned lines should look like this (substitute the appropriate values):
server_address=client_private_IP
allowed_hosts=nagios_server_private_IP
command[check_hda1]=/usr/lib/nagios/plugins/check_disk -w 20% -c 10% -p /dev/vda
Note that there are several other “commands” defined in this file that will run if the Nagios server is configured to use them. Also note that NRPE will be listening on port 5666 because server_port=5666 is set. If you have any firewalls blocking that port, be sure to open it to your Nagios server.
Save and quit.
Restart NRPE
Restart NRPE to put the change into effect:
sudo service nagios-nrpe-server restart
Once you are done installing and configuring NRPE on the hosts that you want to monitor, you will have to add these hosts to your Nagios server configuration before it will start monitoring them.
Add Host to Nagios Configuration
On your Nagios server, create a new configuration file for each of the remote hosts that you want to monitor in /usr/local/nagios/etc/servers/. Replace the highlighted word, “yourhost”, with the name of your host:
sudo vi /usr/local/nagios/etc/servers/yourhost.cfg
Add in the following host definition, replacing the host_name value with your remote hostname (“web-1” in the example), the alias value with a description of the host, and the address value with the private IP address of the remote host:
define host {
use linux-server
host_name yourhost
alias My first Apache server
address 10.132.234.52
max_check_attempts 5
check_period 24x7
notification_interval 30
notification_period 24x7
}
With the configuration file above, Nagios will only monitor if the host is up or down. If this is sufficient for you, save and exit then restart Nagios. If you want to monitor particular services, read on.
Add any of these service blocks for services you want to monitor. Note that the value of check_command determines what will be monitored, including status threshold values. Here are some examples that you can add to your host’s configuration file:
Ping:
define service {
use generic-service
host_name yourhost
service_description PING
check_command check_ping!100.0,20%!500.0,60%
}
SSH (notifications_enabled set to 0 disables notifications for a service):
define service {
use generic-service
host_name yourhost
service_description SSH
check_command check_ssh
notifications_enabled 0
}
If you’re not sure what use generic-service means, it is simply inheriting the values of a service template called “generic-service” that is defined by default.
Now save and quit. Reload your Nagios configuration to put any changes into effect:
sudo service nagios reload
Once you are done configuring Nagios to monitor all of your remote hosts, you should be set. Be sure to access your Nagios web interface, and check out the Services page to see all of your monitored hosts and services:
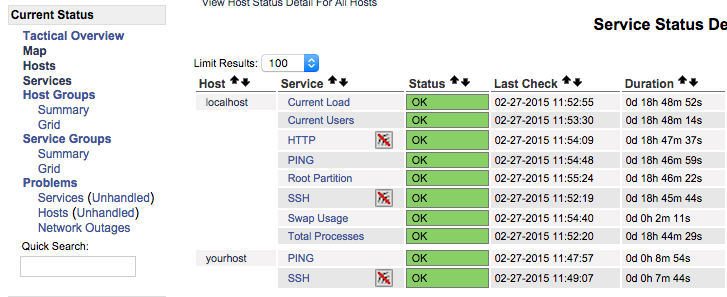
Conclusion
Now that you monitoring your hosts and some of their services, you might want to spend some time to figure out which services are critical to you, so you can start monitoring those. You may also want to set up notifications so, for example, you receive an email when your disk utilization reaches a warning or critical threshold or your main website is down, so you can resolve the situation promptly or before a problem even occurs.
Good luck!
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
This comment has been deleted
This comment has been deleted
Great one this is same in debian or some little things change
I haven’t tried, but it should be similar.
thanks for the reply @manicas but if you can please add some tutorial for Debian because it consumes less ram but this tutorial is great Thanks
I haven’t tried it, but this tutorial is likely to work for Debian too.
how to add Owncloud in nagios to monitor it?
This comment has been deleted
Awesome! I’m a total noob and had no issues beyond a few things on my end that needed to be fixed. Thanks!
Awesome way of explaining, i generally take help with digitalocean tutorials, its very very perfect, thanks for sharing rich knowledge…
hello, Mitchell,
i have created auto installation script, using all your tutorials please check it once
its awesome, the way you have taught…once again thanks…
@ackbote
How are you,
Great tutorial, I wanted to consult you as I arrive me notifications services and host fallen to my email. Thanks in advance for your help.
Hello Mitchell. I just installed Nagios on Ubuntu server 14.04, I followed your tutorial, but when I try to access (http://192.168.1.70/nagios) it show me 404 Not Found.
Note: When I was installing Nagios in the step: sudo ln -s /etc/apache2/sites-available/nagios.conf /etc/apache2/sites-enabled/ I got: "4 /etc/apache2/sites-available/nagios.conf
/etc/apache2/sites-enabled/: total 0
0 000-default.conf" I don’t if it is ok.
And also with the command: sudo ln -s /etc/init.d/nagios /etc/rcS.d/S99nagios I got: “ls: can’t be access to /etc/rcS.d/S99nagios: Not exist the file or directory 8 /etc/init.d/nagios”
The service nagios is running OK and Apache too.
How can I fix it?
Regards Manuel Tapia
Make sure you follow all of the steps in the Install Nagios Core section. In particular:
If you want to uninstall nagios 4 just follow this steps
Hello Mitchell. Thank you for answer me. I issued the commands that you told me again but it doesn’t work yet. What do you suggest me?
I have another question: There must be some files of nagios in: /var/www/html?
Regards Manuel Tapia
Hello! I have configure it too. Working good(Y) . but when my server get down. i’m not getting any email notification. While i’ve configure this: email nagios@localhost ; <<***** CHANGE THIS TO YOUR EMAIL ADDRESS ****** Please suggest what to do? Regards, Amit
Hello Mitchell. I have installed the nagios through your tutorial and I want to monitor the mysql server using nagios core 4.0.8. i couldn’t find the exact configuration document. so please give me a suggesstion. if you have any document pls share to me. its helpful for my configuration.
Thanks in advance for your help
Regards, thiraviam
Do you know how to put the nagios web interface files into the virtual folders created by Virtualmin? We use Virtualmin for our virtual servers, and the setup (with suexec) wont allow any execution of files outside of these accounts. I have moved Nagios web files into the virtual server public_html folder, and they load OK, except there are Internal Server Errors because they are trying to execute scripts outside these folders. Perhaps its the CGI scripts. Thanks
I have added
only_from = 127.0.0.1 192.168.0.115to/etc/xinetd.d/nrpeand restartedxinetd, however when I run/usr/local/nagios/libexec/check_nrpe -H localhostI get the following error message:Running the following after
make allhas fixed the issue for meThis will create
/usr/local/nagios/etc/nrpe.cfg, granted this file does not need to be on the host runningcheck_nrpe, but it is useful for testing.Just a few more observations, if you compile Nagios with
--with-mail=/usr/sbin/sendmailthesendmailcommands it places in/usr/local/nagios/etc/objects/commands.cfgare incorrect and do not work, it will use the command:/usr/bin/sendmail -swhich will result in an error:sendmail: invalid option -- 's'.I have found the quickest and easiest way to configure Nagios to send email notifications is to compile it without
sendmailand simply install (and configure)postfixandmailutils.Actually, all you have to install is
mailutils, that will pull inpostfix.Do you configure nagios notifications? Could you give me a hand? I try it tons of times
After compiling the nagios plugins, there seems to be missing a few plugins, check_mysql and check_mysql_query probably others as well, anyone know what might cause this?
Look at the Define MySQL Process section in this tutorial. You have to add the command to your NRPE client.
Thanks - that could be an alternative fix - although i was more interested in the actual check_mysql plugin. In my setup I have a master/slave replication, and I want the monitoring on both servers. The master acts as the remote server for nagios, where the slave server is the actual nagios monitor. On the remote server, i have installed nagios-nrpe-server and nagios-plugins, which gives me check_mysql and check_mysql_query in /usr/lib/nagios/plugins.
On the montor server, i’ve build nagios and nagios-plugins according to your execellent guide, but in /usr/local/nagios/libexec there are no mysql_check - also in my “build” directory ~/nagios-plugins-2.0.3/plugins i can see there are files like check_load.c, check_load.o which has been built into the check_load executable. But as for check_mysql, there are only the check_mysql.c and check_mysql_query.c, no equal .o files or the final executable.
I revisited this again, and solved it. In case anyone else has had the same problem, in my case the solution (on ubuntu 14.04) was to install
libmysqlclient-devand then./configure --with-nagios-user=nagios --with-nagios-group=nagios --with-openssl --with-mysqlHello,
I followed everything to the tee (I hope so) and everything all went well expect when I try and start nagios. I ran /usr/local/nagios/bin/nagios -v /usr/local/nagios/etc/nagios.cfg to double check my configuration and I see the following message for all the checks I added. Here is one as an example:
Error: Service check command ‘check_nrpe:check_haproxy’ specified in service ‘Haproxy’ for host ‘lb1’ not defined anywhere!
It says this for all the checks I added my self. Did I miss anything I was not aware of? I did the steps all over again and still got the same results.
Thank you in advance for any and all help!
Hello,
I figured out that I had to define the checks in command.cfg before I could use them as checks.
Thanks
Regarding email notifications, when you compile Nagios without setting an email program it will default to using
/bin/mailhowever installingmailutilsorbsd-mailxplacesmailin/usr/bin, therefore you will need to either compile Nagios with--with-mail=/usr/bin/mailor link/usr/bin/mailto/bin/mail.I followed your guide but I have a problem. when I try to log to the web interface i get this: Forbidden
You don’t have permission to access /nagios/ on this server.
Did you follow the step to set up the htpasswd?
Works perfectly well!
Thanks so much for such clear and exact explanations.
Hi,
Thanks for the turorials.
I just have one problem when i try to start nagios (/etc/init.d/nagios start), I have this message :
Starting nagios (via systemctl): nagios.serviceFailed to start nagios.service: Unit nagios.service failed to load: No such file or directory.
Any idea ??
Are you using CentOS 7 by any chance? This tutorial is for Ubuntu 14.04. The CentOS 7 version of this tutorial can be found here.
How do you save and exit the xinetd startup script? Plus the from_only wont go back to green after I edited it. Thanks for awesome tutorial!
If you are using
vionce you have made your changes, pressEscthen type:wqHave you put a space in between
127.0.0.1and your real IP? For example…This comment has been deleted
Hi,
Excellent tutorial! Along with aNag android app I have 24x7 monitoring of my local and remote servers. Could you do a tutorial addressing remote database (mysql) monitoring using for example check_mysql_health? There are blogs detailing this but not very well. They don’t detail if commands need to be run on nagios server or remote server and also permissions for database access are set wide open. You seem to be writing detailed thoughtful articles and the above would be well received.
Thanks,
Madhu
Hey thanks! The Building for Production: Monitoring covers adding monitoring the MySQL process on a remote server. Not sure if that’s what you’re looking for.
I followed this step by step, when I try to start Nagios. I get this error:
“Website: https://www.nagios.org Reading configuration data… Error in configuration file ‘/usr/local/nagios/etc/nagios.cfg’ - Line 452 (Check result path ‘/usr/local/nagios/var/spool/checkresults’ is not a valid directory) Error processing main config file!”
I did see this as well:
"root@ubuntu:~/nagios-4.1.0# sudo make install cd ./base && make install make[1]: Entering directory
/root/nagios-4.1.0/base' make install-basic make[2]: Entering directory/root/nagios-4.1.0/base’ /usr/bin/install -c -m 775 -o nagios -g nagios -d /usr/local/nagios/bin /usr/bin/install -c -m 774 -o nagios -g nagios nagios /usr/local/nagios/bin /usr/bin/install: cannot stat ‘nagios’: No such file or directory make[2]: *** [install-basic] Error 1 make[2]: Leaving directory/root/nagios-4.1.0/base' make[1]: *** [install] Error 2 make[1]: Leaving directory/root/nagios-4.1.0/base’ make: *** [install] Error 2 root@ubuntu:~/nagios-4.1.0# sudo make install-commandmode /usr/bin/install -c -m 775 -o nagios -g nagcmd -d /usr/local/nagios/var/rw chmod g+s /usr/local/nagios/var/rwAhh, I have a lamp stack issue. NM
i followed exact same steps from this article to install nagios on new server. i am getting CHECK_NRPE: Error - Could not complete SSL handshake. /usr/lib/nagios/plugins/check_nrpe -H client1ip CHECK_NRPE: Error - Could not complete SSL handshake
nrpe.cfg file in both locations /usr/local/nagios/etc/nrpe.cfg and /etc/nagios/nrpe.cfg has Code: Select all allowed_hosts=127.0.0.1, 10.0.10.149
if i add new server IP individually to client nrpe.cfg file then no error. But i cant do the same for 100 client hosts. I am trying to solve this error from server side. any suggestions?
Are you editing
/etc/xinetd.d/nrpeon your Nagios server? If so you only need to add your server’s external IP, for exampleonly_from = 127.0.0.1 192.168.0.13.yes i did add /etc/xinetd.d/nrpe only_from = 127.0.0.1 server_ip.
That’s the server taken care of, all you then need to do is edit
/etc/nagios/nrpe.cfgon your monitored servers and editallowed_hostsby adding the IP address of your server (remembering a comma this time) for exampleallowed_hosts=127.0.0.1,192,168,0,13.Don’t forget to restart
xinetdafter editing/etc/xinetd.d/nrpeon your serveri have more than 100 monitoring client hosts on nagios server. do i have to edit etc/nagios/nrpe.cfg individually on them?
Yes, however, if they are all connecting to the same Nagios server, I would suggest using something like Ansible to push
nrpe.cfgto all of your servers.Here is the playbook I use
clients already have nrpe installed. they were being monitored by old nagios server. this is migration from one server to another server. i copied nagios.cfg and all other configurations files from old one to new one and edited the necessary paths and ipaddress. SInce cleints already have everything installed i can just push this alone
is that correct?
What distribution are they running?
They all have different Linux distributions. config options change based on OS and other OS specific variables?
You’ll want to take advantage of playbook conditionals
For example
or
got it. Thank You
i created file for the list of hosts
Changes i want to do
in which path should i create YAML file for playbook and how to create a YAML file?
Save the playbook to
nrpe.ymlthen run…You might want to do a dry run first
Hope this helps
in the same path ? /etc/ansible/nrpe.yml
No, you can save it anywhere, personally I create new folders for each playbook
~/ansible/nrpefor example, thencdto the folder and run the playbookThis comment has been deleted
As Nagios 4.1.0 just been released, if anyone want to upgrade from 4.0.8 simply download the new version (don’t forget to backup before doing this)
Extract it and change to the extracted directory
Configure it, using the same options as before
Compile it
Install Nagios 4.1.0
Finally, restart the service
And you should be all done
Oops, typo
should be
Also, you will need to install
unzipif you don’t already have it installed.Great job, I have Debian 8.2 and already had LAMP installed so I just made my swap and followed the instructions. This was easy with such great command line. I added my Vms from my laptop and picked them up fine.
Thanks for your dedication.
Thanks! I’m glad it worked well for you.
I am having a problem with my Nagios 4.1.1 sending notifications. I have postfix installed and no mail relay and in Nagios 3 on Ubuntu 12.04 this worked. But since migrating to Nagios 4.1.1, Ubuntu 14.04 on new hardware, everything works except notifications. I can send a manual notification at the command prompt and e-mail gets sent. I must be missing something.
My new command.cfg on Nagios 4.1.1, Ubuntu 14,04 lists the following:
‘notify-host-by-email’ command definition
define command{ command_name notify-host-by-email command_line /usr/bin/printf “%b” “***** Nagios ***\n\nNotification Type: $NOTIFICATIONTYPE$\nHost: $HOSTNAME$\nState: $HOSTSTATE$\nAddress: $HOSTADDRESS$\nInfo: $HOSTOUTPUT$\n\nDate/Time: $LONGDATETIME$\n" | /usr/sbin/sendmail -s " $NOTIFICATIONTYPE$ Host Alert: $HOSTNAME$ is $HOSTSTATE$ **” $CONTACTEMAIL$ }
‘notify-service-by-email’ command definition
define command{ command_name notify-service-by-email command_line /usr/bin/printf “%b” “***** Nagios ***\n\nNotification Type: $NOTIFICATIONTYPE$\n\nService: $SERVICEDESC$\nHost: $HOSTALIAS$\nAddress: $HOSTADDRESS$\nState: $SERVICESTATE$\n\nDate/Time: $LONGDATETIME$\n\nAdditional Info:\n\n$SERVICEOUTPUT$\n" | /usr/sbin/sendmail -s " $NOTIFICATIONTYPE$ Service Alert: $HOSTALIAS$/$SERVICEDESC$ is $SERVICESTATE$ **” $CONTACTEMAIL$ }
My older command.cfg setup on Nagios 3, Ubuntu 12.04 was a little different, but it worked.
/usr/bin/printf “%b” “***** Nagios ***\n\nNotification Type: $NOTIFICATIONTYPE$\nHost: $HOSTNAME$\nState: $HOSTSTATE$\nAddress: $HOSTADDRESS$\nInfo: $HOSTOUTPUT$\n\nDate/Time: $LONGDATETIME$\n" | /usr/bin/mail -s " $NOTIFICATIONTYPE$ Host Alert: $HOSTNAME$ is $HOSTSTATE$ **” $CONTACTEMAIL$
I am missing something in my mail config, hope someone can help show me what I am missing.
My /var/log/mail.log, lists the following error:
Sep 24 18:36:35 bg-public postfix/sendmail[21242]: fatal: usage: sendmail [options]
Thanks.
I read a little further and decided to remove the “-s” after /usr/sbin/sendmail and the messages then began to send. However I have no subject line in them ?
I followed this tutorial and deployed nagios in my ubuntu 14 server. But when i access it from web interface i am getting the following error :: In firefox browser : The requested URL /nagios/< was not found on this server. In Chrome : This page requires a web browser which supports frames
@manicas
Hi,
It works great, but one thing:
I got the error: /bin/sh: 1: unzip: not found
Can you add unzip to the packages you should install? Maybe it helps someone else.
Thanks! Done :)
Thanks for a great guide. One thing that kept tripping me up was in the configure and build section, re: adding the optional package: -–with-mail=/usr/sbin/sendmail it may look OK on screen but the -– at the beginning as shown are not two regular hyphens. The second hyphen before with is different… I kept getting a “configure: error: unrecognized option.” It worked once I actually typed it in as shown, rather than copying & pasting it in.
Thanks for catching that. It must have been converted by one of my text editors at some point. I fixed it!
Excellent tutorial. This will work for Debian Jessie as well, but you will want to add the following when you are configuring nagios core (along with any other parameters)
./configure --with-httpd-conf=/etc/apache2/conf.d/nagios.confGreat tutorial! I can’t find a better one on the web! I just don’t get how to use ssl. I’d like both protect Apache using 443 instead of 80 and protect nrpe with ssl. I wish to avoid the server nagios to send and receive unencrypted contents and from the plugins as well. CHECK_NRPE: Error - Could not complete SSL handshake. How do I do it? Thanks in advance
I solved somehow, I don’t get the error anymore when running ./check_nrpe - H hostaddress manually from the server, probably a clean update in my case was necessary. It replies with the version of nrpe. Still, how do I know it uses ssl certificate when launching the commands? and how should somebody protect every command using ssl, if there is no procedure in this tutorial about creating a certificate but only ./configure with ssl? - s it the same, or? - I’m sure I’m missing something.
This command:
Did not work and did not create a sample config file. Where do I get a sample config file?
Great tutorial, thanks!
I’m currently getting compile errors on my Ubuntu 14.04.3 LTS box for plugin version 2.1.1.
Trying to configure
--without-openssland then building gives the following errorI’ve done all the listed apt-gets, and have also tried
... --with-openssl=/usr/bin/openssl.After following these instructions there was a 404 error I kept getting in firefox it was:
Not Found The requested URL /nagios/< was not found on this server.
Which because of the < at the end of the line was a good indication to check the name of the requested url thru network debugger. The php calls were not being evaluated because the installation above skips installing php5-gd and libapache2-mod-php5
These instructions were missing a step for me so in the install build dependencies change:
``` sudo apt-get install build-essential libgd2-xpm-dev openssl libssl-dev xinetd apache2-utils unzip ``
to
sudo apt-get install build-essential libgd2-xpm-dev openssl php5-gd libssl-dev xinetd apache2-utils libapache2-mod-php5 unzipas another note nagios only seems to run correctly in google chrome for now and not in firefox. Has anyone else had the problem of it not running in firefox? is this just because of the iframes issue?
Everything work fine, but I don’t understand the third part of the Nagios 4 setup (installing NRPE from sources with xinetd). Why do we need this ? Can’t we use the “nagios-nrpe-server” package ?
This tutorial is pretty nice. I mainly use Munin but am exploring Nagios for some projects, but two small Apache related things; this a2enmod command:
Can be simplified to be one single command like like this:
Also, the chunk of config related to IP address access seems to be for Apache 2.2 and earlier:
I’m using Ubuntu 14.04 now—after years of using older Ubuntu and Linux installs—and it comes with Apache 2.4 which has a slightly different configuration syntax. So the functional equivalent of those Apache 2.2 directives in Apache 2.4 are:
In this example the
12.0.0.1—and IPv6 equivalent of::1—would suffice, but addinglocalhostto the mix is a decent idea as well. But the old Apache 2.2 format ofOrder deny,allowsimply won’t work for Ubuntu 14.04 since it uses Apache 2.4.How to solve CHECK_NRPE: Socket timeout after 10 seconds error ?? (stuck on this for a long time )
CHECK_NRPE: Socket timeout after 10 seconds. How to fix this error ??
is it possible to run nagios on nginx instead of apache2?
yes
thanks for perfect post i’m using debian 8 and last nagios core 4.1.1 i install nagios exactly according to the instruction but i have an error when start nagios service
Starting nagios (via systemctl): nagios.serviceFailed to start nagios.service: Unit nagios.service failed to load: No such file or directory. failed!
Boss good work. but im having problem while configuring NRPE. plz help.
checking for SSL libraries… configure: error: Cannot find ssl libraries debser-monit:~/nrpe-2.15# ./configure --enable-command-args --with-nagios-user=nagios --with-nagios-group=nagios
Muchas gracias, muy buen instructivo para efectuar la instalación :)
thanks…
Hi Mitchael fantastic article! I have run nagios 4 on ubuntu 14.04 and add my servers to servers folder , and nagios monitor work correctly , but in notification , nagios can’t send email to me on critically alerts. Please help me! thanks a lot.
I followed this it was real good however you referenced nrpe on the host but where is it referenced on the nagios server?
“command[check_hda1]=/usr/lib/nagios/plugins/check_disk -w 20% -c 10% -p /dev/vda”
I am assuming you have to reference this in the yourhost.cfg on the nagios server am I wrong?
Hi How do I see my nagios server IP address? Or how do I set it up? I am done installing the nagios server and want to test it in my browser(Firefox)
Thanks, this documentation is really helpful, please add few more points which make it complete:
and also need php5 installed in system otherwise nagios webpage will not display 2) apt-get install libapache2-mod-php5
After Starting the services, if i try to access "http://<IP_Address>/nagios, Then i am getting like below.
<?php // Allow specifying main window URL for permalinks, etc. $url = ‘main.php’; if (isset($_GET[‘corewindow’])) {
}
i think this is related to nagios folder is not mapped properly.
How can i get map correct one?
what does 'sudo /usr/bin/install -c -m 644 sample-config/httpd.conf /etc/apache2/sites-available/nagios.conf" mean. Kindly elaborate with arguments.
When I runned
maketo install plugins I got it:Hi,
One thing i observed, nothing is described regarding “template”, I meant creating own template.
hello Mitchell, i want to thank you first for this amzing tutorial it’s very simple and easy to follow. i’ve followed it step by step untill the end, some errors occurred but i’ve fix them all, the problem is that at the end all the hosts are down and i dont know what to do, do you have any idea how to fix that ??!!!
Thanks a lot, it worked perfectly.
NRPE 3.0.1 has been released : https://www.nagios.org/news/2016/09/nrpe-3-0-1-released/ I installed it with this tutorial : https://support.nagios.com/kb/article.php?id=515
Mail notification works fine with ssmtp : http://serverfault.com/questions/414947/configuring-nagios-email-notification-using-ssmtp-on-ubuntu I used this commands definition in /usr/local/nagios/etc/objects/commands.cfg :
Brilliant tut, However one question ,can i install all the plugins in in the nagios server machine alone and only nrpe on remote client.I mean if I dont intall plugins on remote client ,will it work.
Thanks very much it was very helpful.
Hi!
Very nice tutorial, thank you very much!
Just one comment, if you are as me following it to install nagios in ubuntu 16 please note that you have to run
Before starting the daemon (sudo service nagios restart) because if you don’t you will see an error from systemd as it does not recognize the service:
it works, really really works, thank you before, but now i got a little problem, how to other user see this monitoring server without admin access? i have created user “support_it” but it seems look like admin access. or perhaps for the other users access not through http://ipserver/nagios ??
Worked seamlessly on AWS Ubuntu 14.04 ( you need to open up the port 5666 between Nagios server and Nagios client. Need to open http from your laptop/source address & ssh port 22 )
Apache2 need to be running on Nagios server apt-get install apache2
In case the Nagios dashboard doesn’t load, issue the below command to install the php apt-get install php5 libapache2-mod-php5 php5-mcrypt
Executed only the 3rd step ( Ignored the server_address and allowed_hosts )
server_address=client_private_IP allowed_hosts=nagios_server_private_IP command[check_hda1]=/usr/lib/nagios/plugins/check_disk -w 20% -c 10% -p /dev/vda ( You might need to change /dev/vda to /dev/xvda1 if you are on AWS )
Need to try few more plugins.
start: Unknown job: nagios how to solve this error?
Why nagios web interface shown html code ?
Hi I follow all the step very carefully. I try 2 time on 2 servers Debian 8 64 bits
When I try the service nagios start I have this error message. Failed to start nagios.service: Unit nagios.service failed to load: No such file or directory.
Any advice on that.
Anyone have fround where to change the ssh check port. I have a custom port for ssh.
I have error on the check_ssh
Hi,
Configuring Nagios with NRPE in this guide has led me to the following error, on both 2.15 and 3.* versions:
root@e1:~/nrpe-3.1.0# make all make: *** No rule to make target ‘all’. Stop. root@e1:~/nrpe-3.1.0# sudo make install make: *** No rule to make target ‘install’. Stop. root@e1:~/nrpe-3.1.0# sudo make install-xinetd make: *** No rule to make target ‘install-xinetd’. Stop. root@e1:~/nrpe-3.1.0# sudo make install-daemon-config make: *** No rule to make target ‘install-daemon-config’. Stop. root@e1:~/nrpe-3.1.0#
I do not want to proceed without correcting this issue.
Environment: Raspbian/Pixel, Debian 7.0 Wheezy, ARM
Please advise
check_nrpecommand was added on the nagios server but its usage was not mentioned; this link has details on how it can be used:https://assets.nagios.com/downloads/nagioscore/docs/nrpe/NRPE.pdf
I get an error when I try to use nrpe to monitor resources on remote server:
I was able to solve it by removing the distribution base NRPE packages mentioned in this article and instead installing the latest version of NRPE (3.2.0 atm) both at the remote host and at the nagios server; after that it worked.
https://support.nagios.com/kb/article.php?id=515
in nagios dashboard nagios host is showing as localhost. How can i display hostname / ip address .
Hello
I did all the steps correctly until the step to configure nagios, in this line command
$ sudo vi /usr/local/nagios/etc/nagios.cfg
This file don’t exist, it appears as a [New File]
Can anyone help me? What am i doing wrong?
Thanks in avance
Following this guide didn’t took me to the successful completion. I had to install below packages. sudo apt-get install wget build-essential apache2 php5-gd libgd2-xpm-dev libapache2-mod-php5
What good is this tutorial if it does not show you how to setup Postfix to send emails and notify when there is issues with hosts/services that Nagios is monitoring?