- Log in to:
- Community
- DigitalOcean
- Sign up for:
- Community
- DigitalOcean

Status: Deprecated
This article covers a version of Ubuntu that is no longer supported. If you are currently operate a server running Ubuntu 12.04, we highly recommend upgrading or migrating to a supported version of Ubuntu:
- Upgrade to Ubuntu 14.04.
- Upgrade from Ubuntu 14.04 to Ubuntu 16.04
- Migrate the server data to a supported version
Reason: Ubuntu 12.04 reached end of life (EOL) on April 28, 2017 and no longer receives security patches or updates. This guide is no longer maintained.
See Instead: This guide might still be useful as a reference, but may not work on other Ubuntu releases. If available, we strongly recommend using a guide written for the version of Ubuntu you are using. You can use the search functionality at the top of the page to find a more recent version.
Introduction
<strong class=“highlight”>Warning: FTP is inherently insecure! Consider <a href=“https://www.digitalocean.com/community/articles/how-to-use-sftp-to-securely-transfer-files-with-a-remote-server”>using SFTP instead of FTP</a>.</strong>
FTP, or file transfer protocol, was a popular way to transfer files between local and remote computers in the past. The protocol is inherently insecure, so its usage has fallen out of favor.
If you still want to use FTP instead of a more secure alternative like SFTP, which uses the SSH protocol to implement file transfers, you can secure it somewhat by configuring FTP to use SSL.
In this guide, we will configure vsftpd to use SSL certificates on an Ubuntu 12.04 VPS.
Install vsftpd
The vsftpd server is available in Ubuntu’s default repositories. You can install it by typing:
sudo apt-get install vsftpd
We now have vsftpd on our server, but we still must configure it.
Configure Basic vsftpd Functionality
The default configuration file is at /etc/vsftpd.conf. Open it with root privileges:
sudo nano /etc/vsftpd.conf
Disable the ability for users to log in anonymously by finding the anonymous_enable parameter and changing it to read “NO”:
<pre> anonymous_enable=<span class=“highlight”>NO</span> </pre>
Next, we need to enable user logins that use the local authentication files, since we disabled anonymous access. Uncomment this line:
local_enable=YES
To enable users to make modifications to the filesystem, we will uncomment the write_enable parameter as well:
write_enable=YES
Additionally, uncomment the chroot_local_user option to restrict users to their own home directories:
chroot_local_user=YES
Save and close the file.
Create an FTP User
Because of the way vsftpd secures its chroot jails, the chroot must not be owned by the user and must not be writeable. Because of this, it is best to implement a user specifically for use with FTP.
Create the user like this:
sudo adduser ftpuser
Assign a password and feel free to press “ENTER” through the other prompts. Now, give root ownership of the ftpuser’s home directory:
sudo chown root:root /home/ftpuser
We need to create a separate directory within this home directory where files can be uploaded. Then, we need to give this directory over to our FTP user:
sudo mkdir /home/ftpuser/files
sudo chown ftpuser:ftpuser /home/ftpuser/files
Now, we should be able to log in (insecurely) as the ftpuser and upload files to the files directory.
Configure SSL with vsftpd
We need to create some SSL certificates to use with vsftpd. We can do this with the following command:
sudo openssl req -x509 -nodes -days 365 -newkey rsa:1024 -keyout /etc/ssl/private/vsftpd.pem -out /etc/ssl/private/vsftpd.pem
This will create a certificate that will last a year. It will be placed in the /etc/ssl/private/ directory, which we can reference in our configuration file.
Add the SSL Details to the vsftpd Configuration
Open the vsftpd configuration file again with root privileges:
sudo nano /etc/vsftpd.conf
Towards the bottom of the file, you should find a line that matches the SSL certificate we just created:
rsa_cert_file=/etc/ssl/private/vsftpd.pem
We will add the additional SSL info below this.
When we created the certificate, we included both the key file and the certificate in one file, so we can also point our private key line to that:
rsa_private_key_file=/etc/ssl/private/vsftpd.pem
After that, we will add the following lines to force SSL. This will restrict clients that can’t deal with TLS, but that is what we want.
ssl_enable=YES
allow_anon_ssl=NO
force_local_data_ssl=YES
force_local_logins_ssl=YES
After this we configure the server to use TLS, which is actually a successor to SSL, and preferred:
ssl_tlsv1=YES
ssl_sslv2=NO
ssl_sslv3=NO
Finally, we will require add some additional options to flesh out our configuration file:
require_ssl_reuse=NO
ssl_ciphers=HIGH
Save and close the file.
Now, we need to restart our server for our changes to take effect:
sudo service vsftpd restart
How To Connect to the Server with FileZilla
Most modern FTP clients can be configured to use SSL and TLS encryption. We will be demonstrating how to connect using FileZilla due to its cross platform support.
In the configuration panel, you should see a button on the far left to open “Site Manager”. Click this:
Click on “New Site” in the bottom right corner of the window interface that appears:
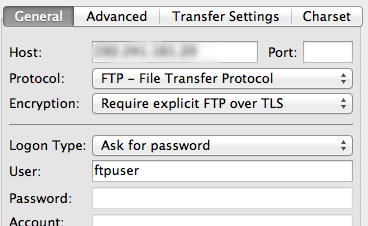
Name the new configuration. Fill out the IP address. Under the “Encryption” drop down menu, select “Require explicit FTP over TLS”.
For “Logon Type”, select “Ask for password”. Fill in the ftp user you created in the “User” field:
Click “Connect” at the bottom of the interface. You will be asked for your user’s password:
You will then be asked to accept the TLS certificate:
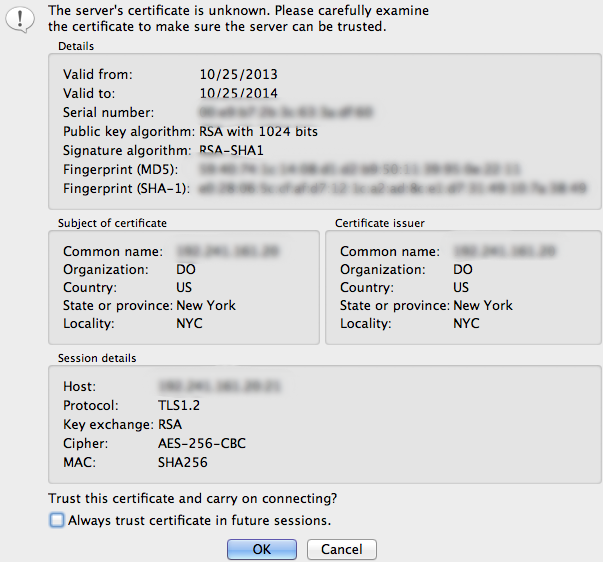
You should now be connected with your server with TLS/SSL encryption.
Conclusion
This setup improves the security of FTP, but it still suffers from insecurity when establishing a connection. If at all possible, it is better to switch to SFTP for these kinds of operations. However, if you do decide to go with FTP, you should make sure to use TLS/SSL whenever possible.
<div class=“author”>By Justin Ellingwood</div>
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
About the author
Former Senior Technical Writer at DigitalOcean, specializing in DevOps topics across multiple Linux distributions, including Ubuntu 18.04, 20.04, 22.04, as well as Debian 10 and 11.
Still looking for an answer?
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
This worked great with the ftpuser however I try to create an additional user and it won’t connect. I get a “Cant read from control socket. Socket error = #0”. ftpuser connect fine, is there anything else that needs to be added besides the additional user with he’s own home folder?
vsftpd.log entries. Thu Dec 12 16:30:34 2013 [pid 2] CONNECT: Client “174.250.xxx.xxx” Thu Dec 12 16:30:38 2013 [pid 1] [raff] OK LOGIN: Client “174.220.xxx.xxx”
This was in the log, raff is the user I am trying to add. I did notice that when I created the user, it also created a user folder /home/raff containing .profile .bashrc and .bash_logout. The /home/ftpuser folder does not have those files.
I just created ftpuser2 and it worked fine (raff still . Is it mandatory that the user name has ftp in it?
Nevermind, got it working. I just deleted the use account and recreated (several times) and finally got it working when I used a shorter password. The original password i was trying to use was 15 characters (numbers and letters). Changed it to less than 8 and it worked.
Problem: I’m able get it to auth/login. It accepts the login, but when Filezilla tries to LiST my /var/www/vhosts/ directory, it fails. I can configure it to work with the regular FTP passive mode, but not with FTP over TLS.
Response: 227 Entering Passive Mode (…) Command: LIST Error: Connection timed out Error: Failed to retrieve directory listing
Using
Limit to user www-ftp
the list of users to give access
userlist_file=/etc/vsftpd.userlist
this list is on
userlist_enable=YES
It is not a list of users to deny ftp access
userlist_deny=NO
Could the user limiting be an issue? I’m also using iptables, but that works fine with regular FTP.
Followed instructions, failed to allow logins with TLS/SSL enabled. Once the encryption-related lines at the bottom of the vsftpd.conf file were commented out, everything worked fine without encryption.
Any suggestions on safely/properly undo-ing what I did with this tutorial so I can restart from the beginning?
Great tutorial, but If I need to connect by console rather than Filezilla ?
Thanks
If you need to connect to the ftp server on the command line, consider using curlftpfs. It allows you to mount the ftp host as a fuse filesystem. See:
http://manpages.ubuntu.com/manpages/precise/man1/curlftpfs.1.html
- Table of contents
- **Status:** Deprecated
- Install vsftpd
- Configure Basic vsftpd Functionality
- Create an FTP User
- Configure SSL with vsftpd
- How To Connect to the Server with FileZilla
- Conclusion
Deploy on DigitalOcean
Click below to sign up for DigitalOcean's virtual machines, Databases, and AIML products.
Become a contributor for community
Get paid to write technical tutorials and select a tech-focused charity to receive a matching donation.
DigitalOcean Documentation
Full documentation for every DigitalOcean product.
Resources for startups and SMBs
The Wave has everything you need to know about building a business, from raising funding to marketing your product.
Get our newsletter
Stay up to date by signing up for DigitalOcean’s Infrastructure as a Newsletter.
New accounts only. By submitting your email you agree to our Privacy Policy
The developer cloud
Scale up as you grow — whether you're running one virtual machine or ten thousand.
Get started for free
Sign up and get $200 in credit for your first 60 days with DigitalOcean.*
*This promotional offer applies to new accounts only.
