Tutorial
How To Configure Bind as an Authoritative-Only DNS Server on Ubuntu 14.04

Introduction
DNS, or the Domain Name System, is often a difficult component to get right when learning how to configure websites and servers. While most people will probably choose to use the DNS servers provided by their hosting company or their domain registrar, there are some advantages to creating your own DNS servers.
In this guide, we will discuss how to install and configure the Bind9 DNS server as authoritative-only DNS servers on Ubuntu 14.04 machines. We will set these up two Bind servers for our domain in a primary-secondary configuration.
Prerequisites and Goals
To complete this guide, you will first need to be familiar with some common DNS terminology. Check out this guide to learn about the concepts we will be implementing in this guide.
You will also need at least two servers. One will be for the “primary” DNS server where the zone files for our domain will originate and one will be the “secondary” server which will receive the zone data through transfers and be available in the event that the other server goes down. This avoids the peril of having a single point of failure for your DNS servers.
Unlike caching or forwarding DNS servers or a multi-purpose DNS server, authoritative-only servers only respond to iterative queries for the zones that they are authoritative for. This means that if the server does not know the answer, it will just tell the client (usually some kind of resolving DNS server) that it does not know the answer and give a reference to a server that may know more.
Authoritative-only DNS servers are often a good configuration for high performance because they do not have the overhead of resolving recursive queries from clients. They only care about the zones that they are designed to serve.
For the purposes of this guide, we will actually be referencing three servers. The two name servers mentioned above, plus a web server that we want to configure as a host within our zone.
We will use the dummy domain example.com for this guide. You should replace it with the domain that you are configuring. These are the details of the machines we will be configuring:
| Purpose | DNS FQDN | IP Address |
|---|---|---|
| Primary name server | ns1.example.com. | 192.0.2.1 |
| Secondary name server | ns2.example.com. | 192.0.2.2 |
| Web Server | www.example.com. | 192.0.2.3 |
After completing this guide, you should have two authoritative-only name servers configured for your domain zones. The names in the center column in the table above will be able to be used to reach your various hosts. Using this configuration, a recursive DNS server will be able to return data about the domain to clients.
Setting the Hostname on the Name Servers
Before we get into the configuration of our name servers, we must ensure that our hostname is configured properly on both our primary and secondary DNS server.
Begin by investigating the /etc/hosts file. Open the file with sudo privileges in your text editor:
sudo nano /etc/hosts
We need to configure this so that it correctly identifies each server’s hostname and FQDN. For the primary name server, the file will look something like this initially:
127.0.0.1 localhost
127.0.1.1 ns1 ns1
. . .
We should modify the second line to reference our specific host and domain combination and point this to our public, static IP address. We can then add the unqualified name as an alias at the end. For the primary server in this example, you would change the second line to this:
127.0.0.1 localhost
192.0.2.1 ns1.example.com ns1
. . .
Save and close the file when you are finished.
We should also modify the /etc/hostname file to contain our unqualified hostname:
sudo nano /etc/hostname
ns1
We can read this value into the currently running system then by typing:
sudo hostname -F /etc/hostname
We want to complete the same procedure on our secondary server.
Start with the /etc/hosts file:
sudo nano /etc/hosts
127.0.0.1 localhost
192.0.2.2 ns2.example.com ns2
Save and close the file when you are finished.
Then, modify the /etc/hostname file. Remember to only use the actual host (just ns2 in our example) for this file:
sudo nano /etc/hostname
ns2
Again, read the file to modify the current system:
sudo hostname -F /etc/hostname
Your servers should now have their host definitions set correctly.
Install Bind on Both Name Servers
On each of your name servers, you can now install Bind, the DNS server that we will be using.
The Bind software is available within Ubuntu’s default repositories, so we just need to update our local package index and install the software using apt. We will also include the documentation and some common utilities:
sudo apt-get update
sudo apt-get install bind9 bind9utils bind9-doc
Run this installation command on your primary and secondary DNS servers to acquire the appropriate files.
Configure the Primary Bind Server
Now that we have the software installed, we can begin by configuring our DNS server on the primary server.
Configuring the Options File
The first thing that we will configure to get started is the named.conf.options file.
The Bind DNS server is also known as named. The main configuration file is located at /etc/bind/named.conf. This file calls on the other files that we will be actually configuring.
Open the options file with sudo privileges in your editor:
sudo nano /etc/bind/named.conf.options
Below, most of the commented lines have been stripped out for brevity, but in general the file should look like this after installation:
options {
directory "/var/cache/bind";
dnssec-validation auto;
auth-nxdomain no; # conform to RFC1035
listen-on-v6 { any; };
};
The main thing that we need to configure in this file is recursion. Since we are trying to set up an authoritative-only server, we do not want to enable recursion on this server. We can turn this off within the options block.
We are also going to default to not allowing transfers. We will override this in individual zone specifications later:
options {
directory "/var/cache/bind";
recursion no;
allow-transfer { none; };
dnssec-validation auto;
auth-nxdomain no; # conform to RFC1035
listen-on-v6 { any; };
};
When you are finished, save and close the file.
Configuring the Local File
The next step that we need to take is to specify the zones that we wish to control this server. A zone is any portion of the domain that is delegated for management to a name server that has not been sub-delegated to other servers.
We are configuring the example.com domain and we are not going to be sub-delegating responsibility for any portion of the domain to other servers. So the zone will cover our entire domain.
To configure our zones, we need to open the /etc/bind/named.conf.local file with sudo privileges:
sudo nano /etc/bind/named.conf.local
This file will initially be empty besides comments. There are other zones that our server knows about for general management, but these are specified in the named.conf.default-zones file.
To start off, we need to configure the forward zone for our example.com domain. Forward zone are the conventional name-to-IP resolution that most of us think of when we discuss DNS. We create a configuration block that defines the domain zone we wish to configure:
zone "example.com" {
};
Note: Many DNS tools, their configuration files, and documentation use the terms “master” and “slave” while DigitalOcean generally prefers alternative descriptors. To avoid confusion we’ve chosen to use the terms “primary” and “secondary” to denote relationships between servers, and only use “master” or “slave” where a configuration directive requires it.
Inside of this block, we add the management information about this zone. We specify the relationship of this DNS server to the zone. This is type master; in the example zone that follows since we are configuring this machine as the primary name server for all of our zones. We also point Bind to the file that holds the actual resource records that define the zone.
We are going to keep our primary zone files in a subdirectory called zones within the Bind configuration directory. We will call our file db.example.com to borrow convention from the other zone files in the Bind directory. Our block will look like this now:
zone "example.com" {
type master;
file "/etc/bind/zones/db.example.com";
};
We want to allow this zone to be transferred to our secondary server, we need to add a line like this:
zone "example.com" {
type master;
file "/etc/bind/zones/db.example.com";
allow-transfer { 192.0.2.2; };
};
Next, we are going to define the reverse zone for our domain.
A Bit About Reverse Zones
If the organization that gave you your IP addresses did not give you a network range and delegate responsibility for that range to you, then your reverse zone file will not be referenced and will be handled by the organization itself.
With hosting providers, the reverse mapping is usually taken care of by the company itself. For instance, with DigitalOcean, reverse mappings for your servers will be automatically created if use the machine’s FQDN as the server name in the control panel. For instance, the reverse mappings for this tutorial could be created by naming the servers like this:

In instances like these, since you have not been allocated a chunk of addresses to administer, you should use this strategy. The strategy outlined below is covered for completeness and to make it applicable if you have been delegated control over larger groups of contiguous addresses.
Reverse zones are used to connect an IP address back to a domain name. However, the domain name system was designed for the forward mappings originally, so some thought is needed to adapt this to allow for reverse mappings.
The pieces of information that you need to keep in mind to understand reverse mappings are:
- In a domain, the most specific portion is of the address is on the left. For an IP address, the most specific portion is on the right.
- The most specific part of a domain specification is either a subdomain or a host name. This is defined in the zone file for the domain.
- Each subdomain can, in turn, define more subdomains or hosts.
All reverse zone mappings are defined under the special domain in-addr.arpa, which is controlled by the Internet Assigned Numbers Authority (IANA). Under this domain, a tree exists that uses subdomains to map out each of the octets in an IP address. To make sure that the specificity of the IP addresses mirrors that of normal domains, the octets of the IP addresses are actually reversed.
So our primary DNS server, with an IP address of 192.0.2.1, would be flipped to read as 1.2.0.192. When we add this host specification as a hierarchy existing under the in-addr.arpa domain, the specific host can be referenced as 1.2.0.192.in-addr.arpa.
Since we define individual hosts (like the leading “1” here) within the zone file itself when using DNS, the zone we would be configuring would be 2.0.192.in-addr.arpa. If our network provider has given us a /24 block of addresses, say 192.0.2.0/24, they would have delegated this in-addr.arpa portion to us.
Now that you know how to specify the reverse zone name, the actual definition is exactly the same as the forward zone. Below the example.com zone definition, make a reverse zone for the network you have been given. Again, this is probably only necessary if you were delegated control over a block of addresses:
zone "2.0.192.in-addr.arpa" {
type master;
file "/etc/bind/zones/db.192.0.2";
};
We have chosen to name the file db.192.0.2. This is specific about what the zone configures and is more readable than the reverse notation.
Save and close the file when you are finished.
Create the Forward Zone File
We have told Bind about our forward and reverse zones now, but we have not yet created the files that will define these zones.
If you recall, we specified the file locations as being within a subdirectory called zones. We need to create this directory:
sudo mkdir /etc/bind/zones
Now, we can use some of the pre-existing zone files in the Bind directory as templates for the zone files we want to create. For the forward zone, the db.local file will be close to what we need. Copy that file into the zones subdirectory with the name used in the named.conf.local file.
sudo cp /etc/bind/db.local /etc/bind/zones/db.example.com
While we are doing this, we can copy a template for the reverse zone as well. We will use the db.127 file, since it’s a close match for what we need:
sudo cp /etc/bind/db.127 /etc/bind/zones/db.192.0.2
Now, open the forward zone file with sudo privileges in your text editor:
sudo nano /etc/bind/zones/db.example.com
The file will look like this:
$TTL 604800
@ IN SOA localhost. root.localhost. (
2 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
@ IN NS localhost.
@ IN A 127.0.0.1
@ IN AAAA ::1
The first thing we need want to do is modify the SOA (start of authority) record that starts with the first @ symbol and continues until the closing parenthesis.
We need to replace the localhost. with the name of the FQDN of this machine. This portion of the record is used to define any name server that will respond authoritatively for the zone being defined. This will be the machine we are configuring now, ns1.example.com. in our case (notice the trailing dot. This is important for our entry to register correctly!).
We also want to change the next piece, which is actually a specially formatted email address with the @ replaced by a dot. We want our emails to go to an administer of the domain, so the traditional email is admin@example.com. We would translate this so it looks like admin.example.com.:
@ IN SOA ns1.example.com. admin.example.com. (
The next piece we need to edit is the serial number. The value of the serial number is how Bind tells if it needs to send updated information to the secondary server.
Note: Failing to increment the serial number is one of the most common mistakes that leads to issues with zone updates. Each time you make an edit, you must bump the serial number.
One common practice is to use a convention for incrementing the number. One approach is to use the date in YYYYMMDD format along with a revision number for the day added onto the end. So the first revision made on June 05, 2014 could have a serial number of 2014060501 and an update made later that day could have a serial number of 2014060502. The value can be a 10 digit number.
It is worth adopting a convention for ease of use, but to keep things simple for our demonstration, we will just set ours to 5 for now:
@ IN SOA ns1.example.com. admin.example.com. (
5 ; Serial
Next, we can get rid of the last three lines in the file (the ones at the bottom that start with @) as we will be making our own.
The first thing we want to establish after the SOA record are the name servers for our zone. We specify the domain and then our two name servers that are authoritative for the zone, by name. Since these name servers will be hosts within the domain itself, it will look a bit self-referential.
For our guide, it will look like this. Again, pay attention to the ending dots!:
; Name servers
example.com. IN NS ns1.example.com.
example.com. IN NS ns2.example.com.
Since the purpose of a zone file is mainly to map host names and services to specific addresses, we are not done yet. Any software reading this zone file is going to want to know where the ns1 and ns2 servers are in order to access the authoritative zones.
So next, we need to create the A records that will associate these name server names to the actual IP addresses of our name servers:
; A records for name servers
ns1 IN A 192.0.2.1
ns2 IN A 192.0.2.2
Now that we have the A records to successfully resolve our name servers to their correct IP addresses, we can add any additional records. Remember, we have a web server on one of our hosts that we want to use to serve our site. We will point requests for the general domain (example.com in our case) to this host, as well as requests for the www host. It will look like this:
; Other A records
@ IN A 192.0.2.3
www IN A 192.0.2.3
You can add any additional hosts that you need to define by creating additional A records. Reference our DNS basics guide to get familiar with some of your options with creating additional records.
When you are finished, your file should look something like this:
$TTL 604800
@ IN SOA ns1.example.com. admin.example.com. (
5 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
; Name servers
example.com. IN NS ns1.example.com.
example.com. IN NS ns2.example.com.
; A records for name servers
ns1 IN A 192.0.2.1
ns2 IN A 192.0.2.2
; Other A records
@ IN A 192.0.2.3
www IN A 192.0.2.3
Save and close the file when you are finished.
Create the Reverse Zone File
Now, we have the forward zone configured, but we need to set up the reverse zone file that we specified in our configuration file. We already created the file at the beginning of the last section.
Open the file in your text editor with sudo privileges:
sudo nano db.192.0.2
The file should look like this:
$TTL 604800
@ IN SOA localhost. root.localhost. (
1 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
@ IN NS localhost.
1.0.0 IN PTR localhost.
We will go through much of the same procedure as we did with the forward zone. First, adjust the domain name, the admin email, and the serial number to match exactly what you had in the last file (The serial number can be different, but should be incremented):
@ IN SOA example.com. admin.example.com. (
5 ; Serial
Again, wipe out the lines under the closing parenthesis of the SOA record. We will be taking the last octet of each IP address in our network range and mapping it back to that host’s FQDN using a PTR record. Each IP address should only have a single PTR record to avoid problems in some software, so you must choose the host name you wish to reverse map to.
For instance, if you have a mail server set up, you probably want to set up the reverse mapping to the mail name, since many systems use the reverse mapping to validate addresses.
First, we need to set our name servers again:
; Name servers
IN NS ns1.example.com.
IN NS ns2.example.com.
Next, you will use the last octet of the IP address you are referring to and point that back to the fully qualified domain name you want to return with. For our example, we will use this:
; PTR Records
1 IN PTR ns1.example.com.
2 IN PTR ns2.example.com.
3 IN PTR www.example.com.
When you are finished, the file should look something like this:
$TTL 604800
@ IN SOA example.com. admin.example.com. (
5 ; Serial
604800 ; Refresh
86400 ; Retry
2419200 ; Expire
604800 ) ; Negative Cache TTL
;
; Name servers
IN NS ns1.example.com.
IN NS ns2.example.com.
; PTR records
1 IN PTR ns1.example.com.
2 IN PTR ns2.example.com.
3 IN PTR www.example.com.
Save and close the file when you are finished.
Testing the Files and Restarting the Service
The configuration for the primary server is now complete, but we still need to implement our changes.
Before we restart our service, we should test all of our configuration files to make sure that they’re configured correctly. We have some tools that can check the syntax of each of our files.
First, we can check the named.conf.local and named.conf.options files by using the named-checkconf command. Since both of these files are source by the skeleton named.conf file, it will test the syntax of the files we modified.
sudo named-checkconf
If this returns without any messages, it means that the named.conf.local and named.conf.options files are syntactically valid.
Next, you can check your individual zone files by passing the domain that the zone handles and the zone file location to the named-checkzone command. So for our guide, you could check the forward zone file by typing:
sudo named-checkzone example.com /etc/bind/zones/db.example.com
If your file has no problems, it should tell you that it loaded the correct serial number and give the “OK” message;
zone example.com/IN: loaded serial 5
OK
If you run into any other messages, it means that you have a problem with your zone file. Usually, the message is quite descriptive about what portion is invalid.
You can check the reverse zone by passing the in-addr.arpa address and the file name. For our demonstration, we would be type this:
sudo named-checkzone 2.0.192.in-addr.arpa /etc/bind/zones/db.192.0.2
Again, this should give you a similar message about loading the correct serial number:
zone 2.0.192.in-addr.arpa/IN: loaded serial 5
OK
If all of your files are checking out, you can restart your Bind service:
sudo service bind9 restart
You should check the logs by typing:
sudo tail -f /var/log/syslog
Keep an eye on this log to make sure that there are no errors.
Configure the Secondary Bind Server
Now that we have the primary server configured, we can go ahead and get the secondary server set up. This will be significantly easier than the primary server.
Configuring the Options File
Again, we will start with the named.conf.options file. Open it with sudo privileges in your text editor:
sudo nano /etc/bind/named.conf.options
We will make the same exact modifications to this file that we made to our primary server’s file.
options {
directory "/var/cache/bind";
recursion no;
allow-transfer { none; };
dnssec-validation auto;
auth-nxdomain no; # conform to RFC1035
listen-on-v6 { any; };
};
Save and close the file when you are finished.
Configuring the Local Configuration File
Next, we will configure the named.conf.local file on the secondary server. Open it with sudo privileges in your text editor:
sudo nano /etc/bind/named.conf.local
Here, we will create each of our zone specifications like we did on our primary server. However, the values and some of the parameters will be different.
First, we will work on the forward zone. Start it off the same way that you did in the primary file:
zone "example.com" {
};
This time, we are going to set the type to slave since this server is acting as a secondary for this zone. This simply means that it receives its zone files through transfer rather than a file on the local system. Additionally, we are just going to specify the relative filename instead of the absolute path to the zone file.
The reason for this is that, for secondary zones, Bind stores the files /var/cache/bind. Bind is already configured to look in this directory location, so we do not need to specify the path.
For our forward zone, these details will look like this:
zone "example.com" {
type slave;
file "db.example.com";
};
Finally, instead of the allow-transfer directive, we will specify the primary servers, by IP address, that this server will accept zone transfers from. This is done in a directive called masters:
zone "example.com" {
type slave;
file "db.example.com";
masters { 192.0.2.1; };
};
This completes our forward zone specification. We can use this same exact format to take care of our reverse zone specification:
zone "2.0.192.in-addr.arpa" {
type slave;
file "db.192.0.2";
masters { 192.0.2.1; };
};
When you are finished, you can save and close the file.
Testing the Files and Restarting the Service
We do not actually have to do any of the actual zone file creation on the secondary machine because, like we mentioned before, this server will receive the zone files from the primary server. So we are ready to test.
Again, we should check the configuration file syntax. Since we don’t have any zone files to check, we only need to use the named-checkconf tool:
sudo named-checkconf
If this returns without any errors, it means that the files you modified have no syntax errors.
If this is the case, you can restart your Bind service:
sudo service bind9 restart
Check the logs on both the primary and secondary servers using:
sudo tail -f /var/log/syslog
You should see some entries that indicate that the zone files have been transferred correctly.
Delegate Authority to your Name Servers
Your authoritative-only name servers should now be completely configured. However, you still need to delegate authority for your domain to your name servers.
To do this, you will have to go to the website where you purchased your domain name. The interface and perhaps the terminology will be different depending on the domain name registrar that you used.
In your domain settings, look for an option that will allow you to specify the name servers you wish to use. Since our name servers are within our domain, this is a special case.
Instead of the registrar simply delegating authority for the zone through the use of NS records, it will need to create a glue record. A glue record is an A record that specifies the IP addresses for the name servers after it specifies the name servers that it is delegating authority to.
Usually, the delegation only lists the name servers that will handle the authority of the domain, but when the name servers are within the domain itself, an A record is needed for the name servers in the parent zone. If this didn’t happen, DNS resolvers would get stuck in a loop because it would never be able to find the IP address of the domain’s name servers to follow the delegation path.
So you need to find a section of your domain registrar’s control panel that allows you to specify name servers and their IP addresses.
As a demonstration, the registrar Namecheap has two different name server sections.
There is a section called “Nameserver Registration” that allows you to specify the IP addresses for name servers within your domain:
Inside, you will be able input the IP addresses of the name servers that exist within the domain:
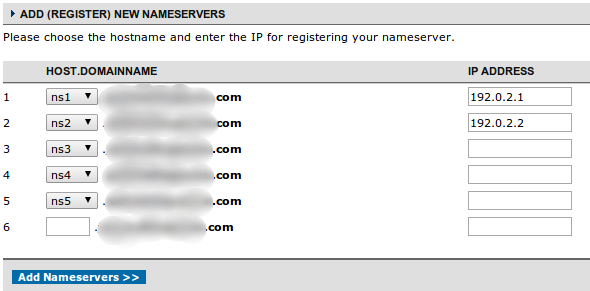
This will create the A record that that serve as the glue records that you need in the parent zone file.
After you’ve done this, you should be able to change the active name servers to your domain’s servers. In NameCheap, this is done using the “Domain Name Server Setup” menu option:
Here, you can tell it to use the name servers you added as the authoritative servers for your site:
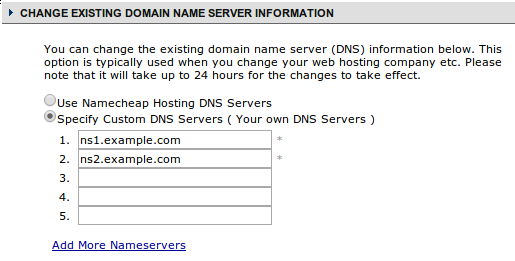
The changes might take awhile to propagate, but you should see the data from your name servers being used within the next 24-48 hours for most registrars.
Conclusion
You should now have two authoritative-only DNS servers configured to server your domains. These can be used to store zone information for additional domains as you acquire more.
Configuring and managing your own DNS servers gives you the most control over how the DNS records are handled. You can make changes and be sure that all relevant pieces of DNS data are up-to-date at the source. While other DNS solutions may make this process easier, it is important to know that you have options and to understand what is happening in more packaged solutions.
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
Tutorial Series: An Introduction to Managing DNS
DNS, or the domain name system, is an essential component of modern internet communication. It allows us to reference computers by names instead of IP addresses. In this series, we will cover the basic ideas behind DNS so that you feel comfortable working with it. Afterwards, we will walk through various ways that you can gain greater control over your domains and DNS resolution.
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
What if ns1 and ns2 are totally on different subnets? For e.g.
ns1
public-ip: 1.2.3.4 internal-ip: 10.1.1.1
ns2
public-ip: 4.3.2.1 internal-ip - 192.168.0.2
If your nameservers are on two different subnets, the reverse zone designation should be the only thing that will give you problems.
On DigitalOcean, the reverse mapping designation are never given to individual servers are taken care of in the control panel by mapping the allocated IP address to the hostname of the machine. This is why we recommend that you use your FQDN for your hostname for public-facing infrastructure.
If you feel like you need two servers with the same subnet, you can try spinning up some additional servers until you get two in the same subnet and then destroying the rest. You can then rename those servers as desired in the control panel and rebuild them to make sure the hostname is propagated to the correct files.
This comment has been deleted
I am currently configuring it on my own machines for learning purpose. Is the reverse zone file will be configured based on internal ip or public ip?
I didn’t understand this part - “On DigitalOcean, the reverse mapping designation are never given to individual servers are taken care of in the control panel by mapping the allocated IP address to the hostname of the machine. This is why we recommend that you use your FQDN for your hostname for public-facing infrastructure.”
Do you mean that if I create two droplets here, then I have to just configure the forward zones for master and slave servers and for reverse mapping, I have to use control panel?
If this is on your own machines, the reverse zone will not be configured automatically. You will have to do that yourself and you will want us whichever IP space that your bind servers are being configured for. So if your ISP has given you a range of public IP addresses, you can set your servers up to be authoritative for that range. Otherwise, for internal networks, you’ll be using the internal IP address since the servers will be set up to resolve only for the internal network.
As for the DigitalOcean-specific part, DigitalOcean allocates one IP address per Droplet and, if you would like to use the DigitalOcean nameservers, you can use the control panel to configure the forward zone info. The reverse mapping is taken care of automatically.
If, in the interface for your domain name registrar, you do not point to DigitalOcean’s DNS servers, you can instead point them to your own authoritative DNS servers. This will allow you to set up the forward zone on your bind servers. However, since DigitalOcean never passes the reverse designation to you (they configure it automatically), you will not be able to control the reverse mapping other than through the name of your hosts. This is done because DigitalOcean does not allocate an entire subnet for each host, and is instead a one-to-one mapping. Other hosts in the same subnet would belong to other customers, so there isn’t a clean way of delegating the authority.
This comment has been deleted
Thanks for the explanation. My ISP has provided one static IP to me and second static IP is from my friend’s ISP. So I have following setup
Public IP1 - 1.2.3.4 (authoritative server) Public IP2 - 1.2.5.6 (slave server)
so I created the reverse zone on my master like this -
zone 2.1.in-addr.arpa{ type master; file “/etc/bind/db.2.1”; allow-transfer { 1.2.5.6; } ; };
in db.2.1, I added PTR like this
4.3 IN PTR host1.mydomain.tld 6.5 IN PTR host2.mydomain.tld
and on slave -
zone 2.1.in-addr.arpa { type slave; file “db.2.1”; masters { 1.2.3.4; }; }
Also for zone transfers, I have to open TCP/UDP port 53 only, no other ports need to be opened?
That looks okay to me. Again though, your ISP probably did not delegate the reverse mappings to your and your friend. That is usually taken care of at a level up from the consumer unless you are given a range of IPs. If you are doing this for practice, it might be best to set up an internal network so that you don’t have to worry about that.
For the zone transfer, that is usually configured to go out on TCP 53, so that should be fine. You can test your zone transfer after you are set up to see if it functions correctly.
Yes, it is not in my hand. I will try with the Internal network later on. I have stopped working on this. Thanks for the great article, it helped me a lot in understanding the DNS.
Hi nice tutorial but for me its a bit confusing
l have server with LAN IP l have also domain name IP And Public IP
so my server
how l should add my A recored and CNAME record also ns1 ip on cpanel
A concise step by step guide to setup my domain nameserver.
Are the slave server settings saved in
/etc/bind/named.conf.local? This is what I get when I save slave server settings in/etc/bind/named.conf.localhello justin,
this you have configured for you LANIP. will there be chnages made when you onfigure for Public IPs. Also How to configure other domain names on the nameservers
@aarav: This can be used in the same way for public or private DNS. Just make sure that your servers are well secured. To configure other domains, you just need to follow the procedure again for your other domains. This will involve adding the additional zone blocks to
/etc/bind/named.conf.localand then creating the actual zone files in/etc/bind/zones/and restarting or reloading the service.when i check intends.com and put my domain name there are lot s error but after install bind9 and follow ur setup i have one ip address(Public Network XXX.xxx.xxx.xxx) so i follow only master slave i didnt do i follow this comment sudo tail -f /var/log/syslog
and get this error please can u tel me whats going on thanks
raid6: using ssse3x2 recovery algorithm Feb 26 13:25:38 sumon kernel: [39220.889427] Request for unknown module key ‘Magrathea: Glacier signing key: af30e7f37b41301c96f985f4789da5f4373e9e92’ err -11 Feb 26 13:25:38 sumon kernel: [39220.889713] xor: automatically using best checksumming function: Feb 26 13:25:38 sumon kernel: [39220.928024] avx : 17311.000 MB/sec Feb 26 13:25:38 sumon kernel: [39220.934775] Request for unknown module key ‘Magrathea: Glacier signing key: af30e7f37b41301c96f985f4789da5f4373e9e92’ err -11 Feb 26 13:25:38 sumon kernel: [39220.952089] Btrfs loaded Feb 26 13:26:05 sumon kernel: [39247.984443] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=220.181.108.171 DST=128.199.235.86 LEN=53 TOS=0x00 PREC=0x00 TTL=44 ID=0 DF PROTO=UDP SPT=23909 DPT=53 LEN=33 Feb 26 13:26:10 sumon kernel: [39252.867735] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=220.181.108.78 DST=128.199.235.86 LEN=53 TOS=0x00 PREC=0x00 TTL=45 ID=0 DF PROTO=UDP SPT=1996 DPT=53 LEN=33 Feb 26 13:27:38 sumon kernel: [39340.049239] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:ff:f0:08:00 SRC=61.160.213.108 DST=128.199.235.86 LEN=40 TOS=0x00 PREC=0x00 TTL=110 ID=2560 PROTO=TCP SPT=33122 DPT=3128 WINDOW=16384 RES=0x00 SYN URGP=0 Feb 26 13:28:10 sumon kernel: [39372.134971] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=220.181.108.101 DST=128.199.235.86 LEN=53 TOS=0x00 PREC=0x00 TTL=44 ID=0 DF PROTO=UDP SPT=51046 DPT=53 LEN=33 Feb 26 13:33:08 sumon kernel: [39670.805400] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=222.186.21.207 DST=128.199.235.86 LEN=40 TOS=0x00 PREC=0x00 TTL=101 ID=256 PROTO=TCP SPT=6000 DPT=5903 WINDOW=16384 RES=0x00 SYN URGP=0
where is error wht my DNS not working :( i cehck intodns.com put my amra.me website
You firewall is blocking the request. Please open the TCP/UDP Port Number 53.
client 128.199.235.86#35766 (2.ubuntu.pool.ntp.org): query (cache) ‘2.ubuntu.pool.ntp.org/A/IN’ denied
This comment has been deleted
Feb 28 02:47:53 sumon named[1526]: client 66.249.66.150#34723 (www.sumon.org): query (cache) ‘www.sumon.org/A/IN’ denied Feb 28 02:52:36 sumon kernel: [ 750.681315] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=58.49.33.178 DST=128.199.235.86 LEN=62 TOS=0x00 PREC=0x00 TTL=49 ID=0 DF PROTO=UDP SPT=53 DPT=60134 LEN=42 Feb 28 02:54:29 sumon named[1526]: client 213.144.48.187#37649 (sumon.org): query (cache) ‘sumon.org/MX/IN’ denied
what does it means my this domain is not working i add fast domain that was works please help me
sudo tail -f /var/log/syslog Feb 28 02:54:31 sumon named[1526]: client 213.144.48.187#11698 (sumon.org): query (cache) ‘sumon.org/MX/IN’ denied Feb 28 02:54:31 sumon named[1526]: client 213.144.48.187#14868 (sumon.org): query (cache) ‘sumon.org/MX/IN’ denied Feb 28 02:57:17 sumon kernel: [ 1031.044021] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:ff:f0:08:00 SRC=85.9.14.1 DST=128.199.235.86 LEN=66 TOS=0x00 PREC=0x00 TTL=55 ID=0 DF PROTO=UDP SPT=53 DPT=60134 LEN=46 Feb 28 02:57:38 sumon kernel: [ 1052.101984] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:ff:f0:08:00 SRC=162.244.35.24 DST=128.199.235.86 LEN=40 TOS=0x00 PREC=0x00 TTL=248 ID=54321 PROTO=TCP SPT=40917 DPT=21320 WINDOW=65535 RES=0x00 SYN URGP=0 Feb 28 02:58:02 sumon kernel: [ 1076.187480] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=89.159.247.56 DST=128.199.235.86 LEN=60 TOS=0x00 PREC=0x00 TTL=53 ID=11890 DF PROTO=TCP SPT=3313 DPT=23 WINDOW=5840 RES=0x00 SYN URGP=0 Feb 28 02:58:05 sumon kernel: [ 1079.186018] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=89.159.247.56 DST=128.199.235.86 LEN=60 TOS=0x00 PREC=0x00 TTL=53 ID=11891 DF PROTO=TCP SPT=3313 DPT=23 WINDOW=5840 RES=0x00 SYN URGP=0 Feb 28 02:58:57 sumon kernel: [ 1131.231305] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=222.186.21.202 DST=128.199.235.86 LEN=40 TOS=0x00 PREC=0x00 TTL=103 ID=256 PROTO=TCP SPT=6000 DPT=208 WINDOW=16384 RES=0x00 SYN URGP=0 Feb 28 02:59:05 sumon kernel: [ 1138.753171] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:ff:f0:08:00 SRC=222.186.31.248 DST=128.199.235.86 LEN=40 TOS=0x00 PREC=0x00 TTL=110 ID=256 PROTO=TCP SPT=47940 DPT=3306 WINDOW=16384 RES=0x00 SYN URGP=0 Feb 28 03:00:15 sumon kernel: [ 1209.327162] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:df:f0:08:00 SRC=96.3.215.190 DST=128.199.235.86 LEN=70 TOS=0x00 PREC=0x00 TTL=115 ID=4528 PROTO=UDP SPT=53 DPT=60134 LEN=50 Feb 28 03:00:45 sumon named[1526]: client 209.105.232.87#39975 (defcon.org): query (cache) ‘defcon.org/ANY/IN’ denied Feb 28 03:03:04 sumon kernel: [ 1378.095492] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:ff:f0:08:00 SRC=185.72.176.143 DST=128.199.235.86 LEN=29 TOS=0x00 PREC=0x00 TTL=54 ID=0 DF PROTO=UDP SPT=53748 DPT=19 LEN=9 Feb 28 03:04:33 sumon kernel: [ 1467.393532] [UFW BLOCK] IN=eth0 OUT= MAC=04:01:40:be:da:01:4c:96:14:ff:ff:f0:08:00 SRC=185.35.62.198 DST=128.199.235.86 LEN=40 TOS=0x00 PREC=0x00 TTL=247 ID=54321 PROTO=UDP SPT=60833 DPT=123 LEN=20 what does it means
Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8)
DO NOT EDIT THIS FILE BY HAND – YOUR CHANGES WILL BE OVERWRITTEN
search amra.me # your private domain nameserver my_ip # ns1 private IP address nameserver my_ip # ns2 private IP address
Master name server ns1.example.com. 192.0.2.1 < this s my Public Network only one ip Slave name server ns2.example.com. 192.0.2.2 << this is my Private Network ip address Web Server www.example.com. 192.0.2.3 << i dont have this ip address
my quis is should i use my private ip address for slave name server or i can user public ip address for my two ns1. , ns2. , ??? please anyone advice me how i should to start config :( becs i config my DNS setting one domain address that only work after i add more 3 domain they don’t work :( they deny like error
client 72.52.104.74#55879 (SUMON.ORG): query (cache) ‘SUMON.ORG/A/IN’ denied client 188.134.0.21#4173 (youngrussian.ru): query (cache) ‘youngrussian.ru/A/IN’ denied client 188.134.0.21#38438 (greenforever.us): query (cache) ‘greenforever.us/A/IN’ denied
:( help needed already 4 days :(
find another problem nslookup my_ip_adress Server: 8.8.8.8 Address: 8.8.8.8#53
** server can’t find resv_ip_adress.in-addr.arpa: NXDOMAIN
sumon@sumon:~$ nslookup amra.me Server: 8.8.8.8 Address: 8.8.8.8#53
Non-authoritative answer: Name: amra.me Address: my_ip
zone 0.in-addr.arpa/IN: loaded serial 1 Feb 28 21:50:06 ns1 named[24049]: zone 235.199.128.in-addr.arpa/IN: loaded serial 5 Feb 28 21:50:06 ns1 named[24049]: zone 127.in-addr.arpa/IN: loaded serial 1 Feb 28 21:50:06 ns1 named[24049]: zone 255.in-addr.arpa/IN: loaded serial 1 Feb 28 21:50:06 ns1 named[24049]: zone localhost/IN: loaded serial 2 Feb 28 21:50:06 ns1 named[24049]: zone amra.me/IN: loaded serial 5 Feb 28 21:50:06 ns1 named[24049]: all zones loaded Feb 28 21:50:06 ns1 named[24049]: running Feb 28 21:50:06 ns1 named[24049]: zone 235.199.128.in-addr.arpa/IN: sending notifies (serial 5) Feb 28 21:50:06 ns1 named[24049]: zone amra.me/IN: sending notifies (serial 5) Feb 28 21:50:52 ns1 named[24049]: client 188.134.0.21#52102 (amra.me): query ‘amra.me/A/IN’ denied Feb 28 21:51:51 ns1 named[24049]: client 188.134.0.21#6454 (greenforever.us): query (cache) ‘greenforever.us/A/IN’ denied Feb 28 21:51:54 ns1 named[24049]: client 74.82.47.32#40290 (dnsscan.shadowserver.org): query (cache) ‘dnsscan.shadowserver.org/A/IN’ denied Feb 28 21:51:58 ns1 named[24049]: client 188.134.0.21#14289 (youngrussian.ru): query (cache) ‘youngrussian.ru/A/IN’ denied
any advice :(
Great tutorial! We are using it, along with another of your tutorials, in class to learn the differences between configuring Recursive, Forwarding and Authoritative name servers, and understanding their behaviors and interactions with other hosts on our private networks. I’ve got one Ubuntu 14.04 LTS VM running as Master, and another as Slave.
However, this example sort of ran out of gas toward the end, in regards to the third server, the web server. I was planning to use the Windows 7 Host, with subset of IIS installed, to perform in this role. Without seeming too naive, were there any specifics you intended to mention regarding configuring the third server, but forgot to include? Besides setting the Windows 7 Host network adapter DNS configuration to the IP addresses of my DNS VMs above, what behavior should I be seeing at my Windows Host?
I don’t have the ability to configure a GLUE record with my Internet provider (Cox), so, viewing the results of the “tail” command you outlined shows only that all my DNS queries return “denied”, and Chrome web browser returns “This webpage is not available”, with Error Codes “DNS_PROBE_FINISHED_NXDOMAIN” and “ERR_CONNECTION_REFUSED”. It appears that the proper behavior between the Master and Slave is occurring as expected, however, with transfers being made to the Slave.
So, I am at a loss as to what further configuration my web server should receive, and what behavior to expect during analysis of a WireShark trace. In the closing sentence of the closing paragraph under “Prerequisites and Goals”, you state, “Using this configuration, a recursive DNS server will be able to return data about the domain to clients.” Do I need a third name server, in a Recursive role, to serve up requests to my Web Server?
nice tutorial. can you please illustrate how to configure sub-domains too. i have a set of bind servers as explained in this tutorial and are working good. i just want to add sub.domain.com also to be served by DNS servers.
Hello, I am getting a strange refusal error.
Master ns1 named[1298]: client 192.168.10.8#46995 (10.168.192.in-addr.arpa): zone transfer ‘10.168.192.in-addr.arpa/AXFR/IN’ denied
What could be happening? Slave 192.168.10.7#53: failed while receiving responses: REFUSED
Any help would be nice.
Nice Tutorial and thanks
Lets say that l wanne host another domain , lets say that l wanne add record for example1.com how can l do that ?
Thanks
I’ve setup my master as slave as follow ns1.dns.example.com ns2.dns.example.com
In my glue records, do I put in ns1.dns.example.com or dns.example.com?
When I ran a nslookup in windows using
“nslookup test.dns.example.com dns.example.com” I can see it got the correct reply and the nameserver received a query.
If I use “nslookup test.dns.example.com ns1.dns.example.com” then I don’t get a reply and I don’t see any query received from the server.
Have I set them up incorrectly?