Tutorial
How To Install WordPress with LEMP on Ubuntu 16.04

Not using Ubuntu 16.04?Choose a different version or distribution.
Introduction
WordPress is the most popular CMS (content management system) on the internet. It allows you to easily set up flexible blogs and websites on top of a MySQL backend with PHP processing. WordPress has seen incredible adoption and is a great choice for getting a website up and running quickly. After setup, almost all administration can be done through the web frontend.
In this guide, we’ll focus on getting a WordPress instance set up on a LEMP stack (Linux, Nginx, MySQL, and PHP) on an Ubuntu 16.04 server.
Prerequisites
In order to complete this tutorial, you will need access to an Ubuntu 16.04 server.
You will need to perform the following tasks before you can start this guide:
- Create a
sudouser on your server: We will be completing the steps in this guide using a non-root user withsudoprivileges. You can create a user withsudoprivileges by following our Ubuntu 16.04 initial server setup guide. - Install a LEMP stack: WordPress will need a web server, a database, and PHP in order to correctly function. Setting up a LEMP stack (Linux, Nginx, MySQL, and PHP) fulfills all of these requirements. Follow this guide to install and configure this software.
- Secure your site with SSL: WordPress serves dynamic content and handles user authentication and authorization. TLS/SSL is the technology that allows you to encrypt the traffic from your site so that your connection is secure. The way you set up SSL will depend on whether you have a domain name for your site.
- If you have a domain name… the easiest way to secure your site is with Let’s Encrypt, which provides free, trusted certificates. Follow our Let’s Encrypt guide for Nginx to set this up.
- If you do not have a domain… and you are just using this configuration for testing or personal use, you can use a self-signed certificate instead. This provides the same type of encryption, but without the domain validation. Follow our self-signed SSL guide for Nginx to get set up.
When you are finished the setup steps, log into your server as your sudo user and continue below.
Step 1: Create a MySQL Database and User for WordPress
The first step that we will take is a preparatory one. WordPress uses MySQL to manage and store site and user information. We have MySQL installed already, but we need to make a database and a user for WordPress to use.
To get started, log into the MySQL root (administrative) account by issuing this command:
You will be prompted for the password you set for the MySQL root account when you installed the software.
First, we can create a separate database that WordPress can control. You can call this whatever you would like, but we will be using wordpress in this guide to keep it simple. You can create the database for WordPress by typing:
Note
Every MySQL statement must end in a semi-colon (;). Check to make sure this is present if you are running into any issues.
Next, we are going to create a separate MySQL user account that we will use exclusively to operate on our new database. Creating one-function databases and accounts is a good idea from a management and security standpoint. We will use the name wordpressuser in this guide. Feel free to change this if you’d like.
We are going to create this account, set a password, and grant access to the database we created. We can do this by typing the following command. Remember to choose a strong password here for your database user:
You now have a database and user account, each made specifically for WordPress. We need to flush the privileges so that the current instance of MySQL knows about the recent changes we’ve made:
Exit out of MySQL by typing:
Step 2: Adjust Nginx’s Configuration to Correctly Handle WordPress
Next, we will be making a few minor adjustments to our Nginx server block files.
Open the default server block file with sudo privileges to begin:
Within the main server block, we need to add a few location blocks.
Start by creating exact-matching location blocks for requests to /favicon.ico and /robots.txt, both of which we do not want to log requests for.
We will use a regular expression location to match any requests for static files. We will again turn off the logging for these requests and will mark them as highly cacheable since these are typically expensive resources to serve. You can adjust this static files list to contain any other file extensions your site may use:
server {
. . .
location = /favicon.ico { log_not_found off; access_log off; }
location = /robots.txt { log_not_found off; access_log off; allow all; }
location ~* \.(css|gif|ico|jpeg|jpg|js|png)$ {
expires max;
log_not_found off;
}
. . .
}
Inside of the existing location / block, we need to adjust the try_files list so that instead of returning a 404 error as the default option, control is passed to the index.php file with the request arguments.
This should look something like this:
server {
. . .
location / {
#try_files $uri $uri/ =404;
try_files $uri $uri/ /index.php$is_args$args;
}
. . .
}
When you are finished, save and close the file.
Now, we can check our configuration for syntax errors by typing:
If no errors were reported, reload Nginx by typing:
Step 3: Install Additional PHP Extensions
When setting up our LEMP stack, we only required a very minimal set of extensions in order to get PHP to communicate with MySQL. WordPress and many of its plugins leverage additional PHP extensions.
We can download and install some of the most popular PHP extensions for use with WordPress by typing:
Note
Each WordPress plugin has its own set of requirements. Some may require additional PHP packages to be installed. Check your plugin documentation to discover its PHP requirements. If they are available, they can be installed with apt-get as demonstrated above.
When you are finished installing the extensions, restart the PHP-FPM process so that the running PHP processor can leverage the newly installed features:
Step 4: Download WordPress
Now that our server software is configured, we can download and set up WordPress. For security reasons in particular, it is always recommended to get the latest version of WordPress from their site.
Change into a writable directory and then download the compressed release by typing:
Extract the compressed file to create the WordPress directory structure:
We will be moving these files into our document root momentarily. Before we do that, we can copy over the sample configuration file to the filename that WordPress actually reads:
We can also create the upgrade directory, so that WordPress won’t run into permissions issues when trying to do this on its own following an update to its software:
Now, we can copy the entire contents of the directory into our document root. We are using the -a flag to make sure our permissions are maintained. We are using a dot at the end of our source directory to indicate that everything within the directory should be copied, including any hidden files:
Step 5: Configure the WordPress Directory
Before we do the web-based WordPress setup, we need to adjust some items in our WordPress directory.
Adjusting the Ownership and Permissions
One of the big things we need to accomplish is setting up reasonable file permissions and ownership. We need to be able to write to these files as a regular user, and we need the web server to also be able to access and adjust certain files and directories in order to function correctly.
We’ll start by assigning ownership over all of the files in our document root to our username. We will use sammy as our username in this guide, but you should change this to match whatever your sudo user is called. We will assign group ownership to the www-data group:
Next, we will set the setgid bit on each of the directories within the document root. This causes new files created within these directories to inherit the group of the parent directory (which we just set to www-data) instead of the creating user’s primary group. This just makes sure that whenever we create a file in the directory on the command line, the web server will still have group ownership over it.
We can set the setgid bit on every directory in our WordPress installation by typing:
There are a few other fine-grained permissions we’ll adjust. First, we’ll give group write access to the wp-content directory so that the web interface can make theme and plugin changes:
As part of this process, we will give the web server write access to all of the content in these two directories:
This should be a reasonable permissions set to start with. Some plugins and procedures might require additional tweaks.
Setting up the WordPress Configuration File
Now, we need to make some changes to the main WordPress configuration file.
When we open the file, our first order of business will be to adjust some secret keys to provide some security for our installation. WordPress provides a secure generator for these values so that you do not have to try to come up with good values on your own. These are only used internally, so it won’t hurt usability to have complex, secure values here.
To grab secure values from the WordPress secret key generator, type:
You will get back unique values that look something like this:
Warning
It is important that you request unique values each time. Do NOT copy the values shown below!
Outputdefine('AUTH_KEY', '1jl/vqfs<XhdXoAPz9 DO NOT COPY THESE VALUES c_j{iwqD^<+c9.k<J@4H');
define('SECURE_AUTH_KEY', 'E2N-h2]Dcvp+aS/p7X DO NOT COPY THESE VALUES {Ka(f;rv?Pxf})CgLi-3');
define('LOGGED_IN_KEY', 'W(50,{W^,OPB%PB<JF DO NOT COPY THESE VALUES 2;y&,2m%3]R6DUth[;88');
define('NONCE_KEY', 'll,4UC)7ua+8<!4VM+ DO NOT COPY THESE VALUES #`DXF+[$atzM7 o^-C7g');
define('AUTH_SALT', 'koMrurzOA+|L_lG}kf DO NOT COPY THESE VALUES 07VC*Lj*lD&?3w!BT#-');
define('SECURE_AUTH_SALT', 'p32*p,]z%LZ+pAu:VY DO NOT COPY THESE VALUES C-?y+K0DK_+F|0h{!_xY');
define('LOGGED_IN_SALT', 'i^/G2W7!-1H2OQ+t$3 DO NOT COPY THESE VALUES t6**bRVFSD[Hi])-qS`|');
define('NONCE_SALT', 'Q6]U:K?j4L%Z]}h^q7 DO NOT COPY THESE VALUES 1% ^qUswWgn+6&xqHN&%');
These are configuration lines that we can paste directly in our configuration file to set secure keys. Copy the output you received now.
Now, open the WordPress configuration file:
Find the section that contains the dummy values for those settings. It will look something like this:
. . .
define('AUTH_KEY', 'put your unique phrase here');
define('SECURE_AUTH_KEY', 'put your unique phrase here');
define('LOGGED_IN_KEY', 'put your unique phrase here');
define('NONCE_KEY', 'put your unique phrase here');
define('AUTH_SALT', 'put your unique phrase here');
define('SECURE_AUTH_SALT', 'put your unique phrase here');
define('LOGGED_IN_SALT', 'put your unique phrase here');
define('NONCE_SALT', 'put your unique phrase here');
. . .
Delete those lines and paste in the values you copied from the command line:
. . .
define('AUTH_KEY', 'VALUES COPIED FROM THE COMMAND LINE');
define('SECURE_AUTH_KEY', 'VALUES COPIED FROM THE COMMAND LINE');
define('LOGGED_IN_KEY', 'VALUES COPIED FROM THE COMMAND LINE');
define('NONCE_KEY', 'VALUES COPIED FROM THE COMMAND LINE');
define('AUTH_SALT', 'VALUES COPIED FROM THE COMMAND LINE');
define('SECURE_AUTH_SALT', 'VALUES COPIED FROM THE COMMAND LINE');
define('LOGGED_IN_SALT', 'VALUES COPIED FROM THE COMMAND LINE');
define('NONCE_SALT', 'VALUES COPIED FROM THE COMMAND LINE');
. . .
Next, we need to modify some of the database connection settings at the beginning of the file. You need to adjust the database name, the database user, and the associated password that we configured within MySQL.
The other change we need to make is to set the method that WordPress should use to write to the filesystem. Since we’ve given the web server permission to write where it needs to, we can explicitly set the filesystem method to “direct”. Failure to set this with our current settings would result in WordPress prompting for FTP credentials when we perform some actions.
This setting can be added below the database connection settings, or anywhere else in the file:
. . .
define('DB_NAME', 'wordpress');
/** MySQL database username */
define('DB_USER', 'wordpressuser');
/** MySQL database password */
define('DB_PASSWORD', 'password');
. . .
define('FS_METHOD', 'direct');
Save and close the file when you are finished.
Step 6: Complete the Installation Through the Web Interface
Now that the server configuration is complete, we can complete the installation through the web interface.
In your web browser, navigate to your server’s domain name or public IP address:
http://server_domain_or_IP
Select the language you would like to use:
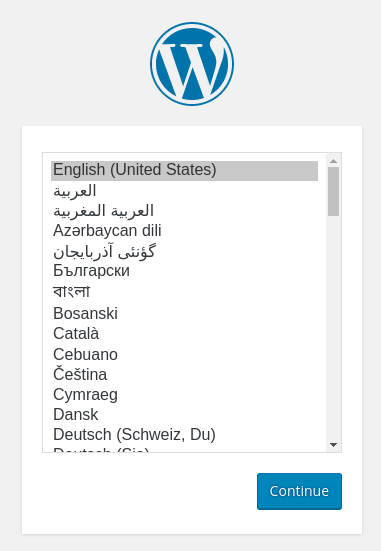
Next, you will come to the main setup page.
Select a name for your WordPress site and choose a username (it is recommended not to choose something like “admin” for security purposes). A strong password is generated automatically. Save this password or select an alternative strong password.
Enter your email address and select whether you want to discourage search engines from indexing your site:
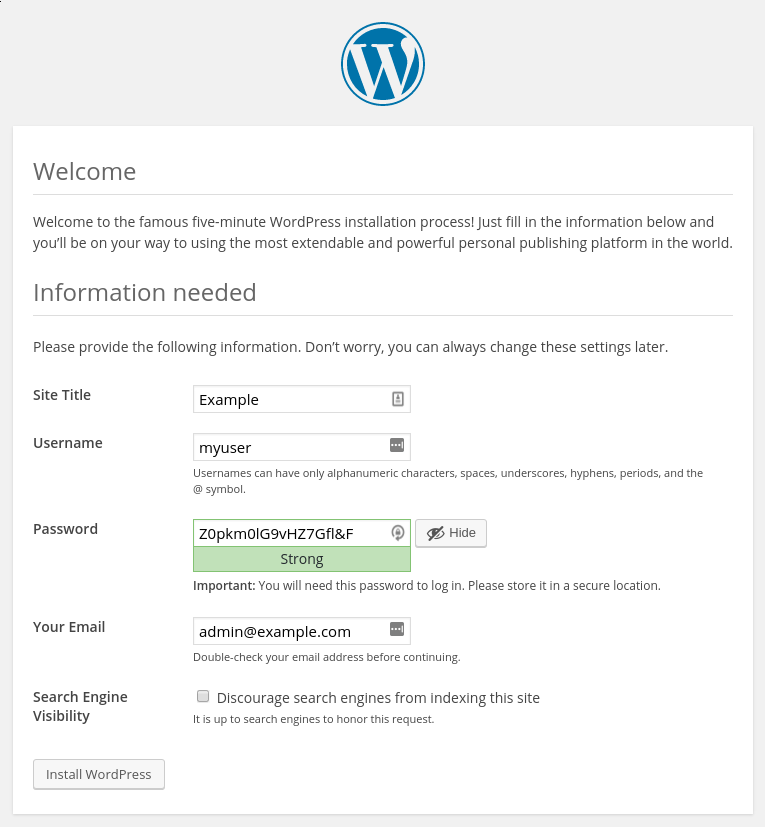
When you click ahead, you will be taken to a page that prompts you to log in:
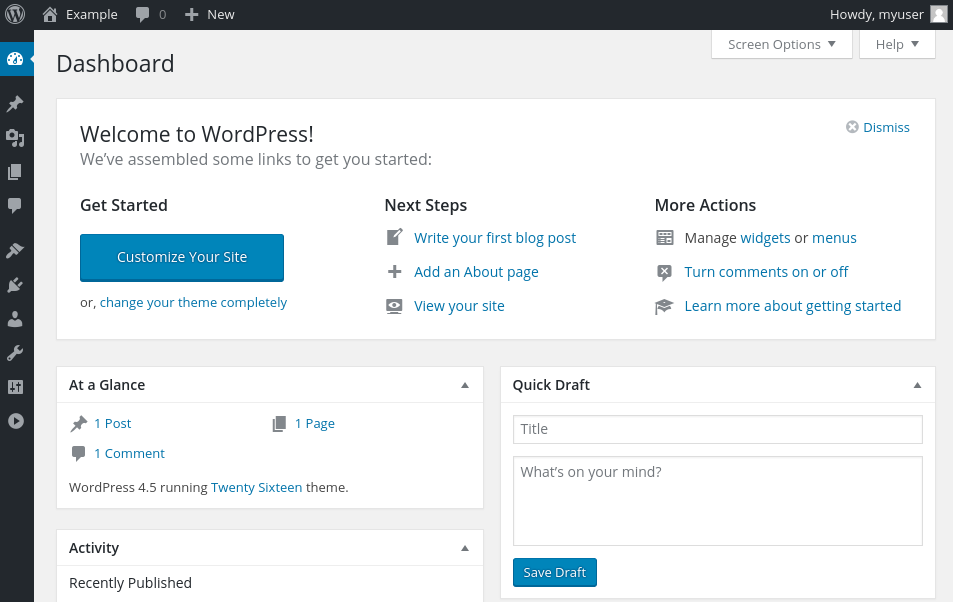
Once you log in, you will be taken to the WordPress administration dashboard:
Upgrading WordPress
As WordPress upgrades become available, you will be unable in install them through the interface with the current permissions.
The permissions we selected here are meant to provide a good balance between security and usability for the 99% of times between upgrading. However, they are a bit too restrictive for the software to automatically apply updates.
When an update becomes available, log back into your server as your sudo user. Temporarily give the web server process access to the whole document root:
Now, go back the WordPress administration panel and apply the update.
When you are finished, lock the permissions down again for security:
This should only be necessary when applying upgrades to WordPress itself.
Conclusion
WordPress should be installed and ready to use! Some common next steps are to choose the permalinks setting for your posts (can be found in Settings > Permalinks) or to select a new theme (in Appearance > Themes). If this is your first time using WordPress, explore the interface a bit to get acquainted with your new CMS.
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
Excellent documentation squire. The most thorough treatment of installing WordPress from scratch that I’ve seen. Adjusting ownership & permissions is crucial and is often skated over superficially – these explanations really help understand what’s needed & enable people to fix permission problems (not that they are likely to happen). One suggested amendment :
I always give an explicit character set and collation when creating the database to avoid any problems later. So :
Just a thought.
markpea
@markpea: Thanks for the feedback! Also, excellent advice. I updated the article to include your suggestion. Being explicit about the encoding is definitely a step in the right directly. Thanks!
Hello;
Do you mind giving us the FULL conf? /etc/nginx/sites-available/default
@iamkingsleyf: Hello. Your
/etc/nginx/sites-available/defaultfile will vary depending on how you’ve modified it in the past. In the context of this guide, this mainly means the difference between whether you followed the Let’s Encrypt prerequisite or the self-signed certificate one.If you used the Let’s Encrypt guide, it will likely look something like this when you are finished. If, on the other hand, you followed the self-signed guide, your server block would probably end up looking a bit more like this.
I’ll be working in the next week or two to standardize these two procedures so that their recommendations are more aligned. Hope that helps.
Thanks… i will try this out
I use Let’s Encrypt in my Nginx Server Blocks (Virtual Hosts). and I try to install Wordpress with this tutorial, but I got error
“nginx: [emerg] the size 52428800 of shared memory zone “SSL” conflicts with already declared size 10485760 in /etc/nginx/sites-enabled/puppymemo.com:46 nginx: configuration file /etc/nginx/nginx.conf test failed”.
when I change “ssl_session_cache shared:SSL:50m;” to “ssl_session_cache shared:SSL:10m;”, I got another error
“nginx: [emerg] BIO_new_file(”/etc/letsencrypt/live/www.puppymemo.com.com/fullchain.pem") failed (SSL: error:02001002:system library:fopen:No such file or directory:fopen(‘/etc/letsencrypt/live/www.puppymemo.com.com/fullchain.pem’,‘r’) error:2006D080:BIO routines:BIO_new_file:no such file) nginx: configuration file /etc/nginx/nginx.conf test failed"
How can I solve it? T^T
Good, Thanks
I assume this is the php 7 installation of your series with LEMP stack? If so, how much faster is it compared to the DO 1-click install of 14.04 worpdress package?
Any recommendations on further tweaking for speed, cache, etc?
Thank you for a great series on how to do things!
For WordPress some additional packages for PHP7 are needed, not covered in LEMP tutorial. At least php7-xml and GD or Imagick. Possibly all of these ‘apt-get install php7.0-fpm php7.0-mysql php7.0-curl php7.0-gd php7.0-json php7.0-mcrypt php7.0-opcache php7.0-xml’? Copied from another tutorial.
@arijuki: Thanks for the heads up!
WordPress as an organization is very evasive in answering the question of which PHP extensions should be installed. The general answer is that they don’t strictly need any of them, but can leverage some of them if they are available. That makes the decision of which to install a bit tricky. The plugin question further complicates this.
That being said, I’ve edited the article to include a step that includes some of the more common ones. Thanks for pointing that out!
It appears that the tutorial says:
sudo apt-get install php-curl php-gd php-mbstring php-mcrypt php-xml php-xmlrpc
When the proper command would be:
sudo apt-get install php7.0-curl php7.0-gd php7.0-mbstring php7.0-mcrypt php7.0-xml php7.0-xmlrpc
Just pointing it out. Thank you!
hey which version of lemp should i use? 16.04 or 14.04 ? i am gonna install wordpress on it.
I migrated my Drupal7 sites from centos7 to ubuntu16 with the help of this guide. Now Drupal sites don’t send emails after registration or in the other events. I tried to setup postfix with different options yet no result. Will you please advice what are the modifications or settings to be done? There was no additional setup required when it was in CentOS.
I solved the issue by reinstalling postfix with the help of this. Now it works as expected.
You can use this stack script for one click lemp + wordpress installation :
https://github.com/mirzazeyrek/lemp-wordpress-stack
This comment has been deleted
@jellingwood So what is your recommendation if I DO want automatic updates and don’t want to manually keep chown-ing the document root?
WP permission issues always seem to crop up when a non www-data user owns the WordPress files and I haven’t yet found a good tutorial that strikes the balance that I actually want, which is having it owned by a non-priviledged user but still able to auto update wordpress core.
@riolowry - Did you ever find a nice way to accomplish this?
None of these tutorials work for me.
Hmm, got to the end of step 5, and when I browse to my server’s IP, I’m still seeing the Nginx welcome page. Am I supposed to move some files from /etc/nginx/sites-available/ to /etc/nginx/sites-enabled ?
I reviewed my steps, and my issue was in my /etc/nginx/sites-available/default file. Thanks for posting above what you ended up with the file, as I was able to tell that I had put lines in the incorrect blocks. All is good now :)
Thanks for this awesome tutorial. At first time, It was complete failure at this point “Nginx default server block file” while editing. I failed to identify the error, after that completely destroyed that droplet and started with fresh droplet. I took almost like seven hours for me to get live. PS: A complete newbie here . Thank you :)
Thank you for putting this tutorial together.
I am currently attempting to install wordpress on my default LEMP Droplet and it’s giving is issues.
Then I had issues with “apt-get install php-curl php-gd php-mbstring php-mcrypt php-xml php-xmlrpc”
This command came back with:
" Reading package lists… Done Building dependency tree Reading state information… Done E: Unable to locate package php-curl E: Unable to locate package php-gd E: Unable to locate package php-mbstring E: Unable to locate package php-mcrypt E: Unable to locate package php-xml E: Unable to locate package php-xmlrpc "
This is how far I got with the installation and have no idea what is giving me these errors on the one click LEMP Droplet.
Follow up - I just noticed that the default one click LEMP Droplet is 14.04 and this tutorial is for 16.04.
Thank you anyway.
I get this error (http://imgur.com/hDUiJch) when I run the command:
Any ideas?? I followed the tutorial exactly to this point. Curl is installed.
Answer pointed out here
wget https://wordpress.org/latest.tar.gz worked for me
It’s probably a good idea to disable xmlrpc.php to protect against DDOS attacks. More at https://www.digitalocean.com/community/tutorials/how-to-protect-wordpress-from-xml-rpc-attacks-on-ubuntu-14-04
Hi! Great tutorial, really enjoyed it -
I am having getting a ‘404 not found’ error from nginx.
I’m running Ubuntu 16.04 LEMP server, was working fine - tested phpinfo and was OK until I edited …/sites-available/default I deleted modified default file and restored a backup and now it still doesn’t work (phpinfo file showing 404 error as well).
Any ideas what might have happened?
Thanks! -Avery
Step 6: Complete the Installation Through the Web Interface
I have gotten to Step 6 with no errors and no omissions yet when I visit my site I only see the “Welcome to niginx!” page. What’s going on?
It seems the
GRANTstatement in the mysql command below is deprecated and no longer works.Here’s the error I’m getting:
Can someone please provide me with the new way to do this.
It should be GRANT ALL PRIVILEGES on wordpress.* etc.
I find multiple references that say to do the following, is it not important to do that?
The wp-config.php is an important file as it contains your database connection settings, table prefix, security keys, and other sensitive information.
To deny public access to
wp-config.php, go in the file/etc/nginx/sites-available/defaultand add the following code inside theserver { }block:This was an amazing tutorial. yeah, I have setup WordPress on a vps for the first time in my life :) **Thank you very much Justing **
Great tutorial as always Justin. One thing that seems to be missing is any mention of the need for the following line to be added in your nginx sites-available file:
I guess that is already included in the default file?
Great tutorial.
I followed these tutorials step by step and got it all working initial server setup guide Install a LEMP stack Install ssl with LetsEncrypt.
In none of these was any mail client installed to be used by wordpress. Is this no longer necessary with the latest wordpress and ubuntu 16.04?
Cheers,
Ramiro
Could I request a full server block example from someone?
I continue to download index.php. Mine is as follows:
Thanks in advance for any help!
This comment has been deleted
I was not able to install any plugins after completing this tutorial and I couldn’t figure it out for a while. Turns out, you need to add the write permission for the ‘www-data’ group on the wp-content/upgrade folder for installing plugins as well. I think you may have missed that above.
EDIT : I’m refering to installing the plugins from Wordpress’s admin dashboard, not manually.
Noticed I couldn’t install/update plugins via the WordPress admin.
While not mentioned in the article, adding write access to the upgrade folder solves this: sudo chmod g+w /var/www/html/wp-content/upgrade
Please update how the final nginx page should look like, under the sites-available/default page
I followed this tutorial and at the end of it I get the 404 page. I had
in but that was giving the generic 404 - so I went back to
and I get a custom 404 I built. HOWEVER I am not getting the Wordpress index.php (gives the 404) but I can get the default DigitalOcean index.html
Thank you for this tutorial.
I’m facing a strange issue and I don’t know how to solve it. I already have my own server with 4 services on it (website, plex …) everything running smoothly with nginx and a SSL certificat thank to Let’s Encrypt.
I follow this documentation and change juste what I needed (like
wp.mydomain.comfor nginx).I keep listening on 80 for this subdomain. And I didn’t add a certifical for this url.
But when I’m trying to access
wp.mydomain.comall my browser told me that my connection is not private with the error :NET::ERR_CERT_COMMON_NAME_INVALIDAny idea why ?