Tutorial
How To Configure OCSP Stapling on Apache and Nginx

Introduction
OCSP stapling is a TLS/SSL extension which aims to improve the performance of SSL negotiation while maintaining visitor privacy. Before going ahead with the configuration, a short brief on how certificate revocation works. This article uses free certificates issued by StartSSL to demonstrate.
This tutorial will use the base configuration for Apache and Nginx outlined below:
- How To Set Up Multiple SSL Certificates on One IP with Apache on Ubuntu 12.04
- How To Set Up Multiple SSL Certificates on One IP with Nginx on Ubuntu 12.04
About OCSP
OCSP (Online Certificate Status Protocol) is a protocol for checking if a SSL certificate has been revoked. It was created as an alternative to CRL to reduce the SSL negotiation time. With CRL (Certificate Revocation List) the browser downloads a list of revoked certificate serial numbers and verifies the current certificate, which increases the SSL negotiation time. In OCSP the browser sends a request to a OCSP URL and receives a response containing the validity status of the certificate. The following screenshot shows the OCSP URI of digitalocean.com.

About OCSP stapling
OCSP has major two issues: privacy and heavy load on CA’s servers.
Since OCSP requires the browser to contact the CA to confirm certificate validity it compromises privacy. The CA knows what website is being accessed and who accessed it.
If a HTTPS website gets lots of visitors the CA’s OCSP server has to handle all the OCSP requests made by the visitors.
When OCSP stapling is implemented the certificate holder (read web server) queries the OCSP server themselves and caches the response. This response is “stapled” with the TLS/SSL Handshake via the Certificate Status Request extension response. As a result the CA’s servers are not burdened with requests and browsers no longer need to disclose users’ browsing habits to any third party.
Check for OCSP stapling support
OCSP stapling is supported on
- Apache HTTP Server (>=2.3.3)
- Nginx (>=1.3.7)
Please check the version of your installation with the following commands before proceeding.
Apache:
apache2 -v
Nginx:
nginx -v
CentOS/Fedora users replace apache2 with httpd.
Retrieve the CA bundle
Retrieve the root CA and intermediate CA’s certificate in PEM format and save them in a single file. This is for StartSSL’s Root and Intermediate CA certificates.
cd /etc/ssl
wget -O - https://www.startssl.com/certs/ca.pem https://www.startssl.com/certs/sub.class1.server.ca.pem | tee -a ca-certs.pem> /dev/null
If your CA provides certificates in DER format convert them to PEM. For example DigiCert provides certificates in DER format. To download them and convert to PEM use the following commands:
cd /etc/ssl
wget -O - https://www.digicert.com/CACerts/DigiCertHighAssuranceEVRootCA.crt | openssl x509 -inform DER -outform PEM | tee -a ca-certs.pem> /dev/null
wget -O - https://www.digicert.com/CACerts/DigiCertHighAssuranceEVCA-1.crt | openssl x509 -inform DER -outform PEM | tee -a ca-certs.pem> /dev/null
Both sets of commands use tee to write to the file, so you can use sudo tee if logged in as a non-root user.
Configuring OCSP Stapling on Apache
Edit the SSL virtual hosts file and place these lines inside the <VirtualHost></VirtualHost> directive.
sudo nano /etc/apache2/sites-enabled/example.com-ssl.conf
SSLCACertificateFile /etc/ssl/ca-certs.pem
SSLUseStapling on
A cache location has to be specified outside <VirtualHost></VirtualHost>.
sudo nano /etc/apache2/sites-enabled/example.com-ssl.conf
SSLStaplingCache shmcb:/tmp/stapling_cache(128000)
If you followed this article to setup SSL sites on Apache, the virtual host file will look this:
/etc/apache2/sites-enabled/example.com-ssl.conf
<IfModule mod_ssl.c>
SSLStaplingCache shmcb:/tmp/stapling_cache(128000)
<VirtualHost *:443>
ServerAdmin webmaster@localhost
ServerName example.com
DocumentRoot /var/www
SSLEngine on
SSLCertificateFile /etc/apache2/ssl/example.com/apache.crt
SSLCertificateKeyFile /etc/apache2/ssl/example.com/apache.key
SSLCACertificateFile /etc/ssl/ca-certs.pem
SSLUseStapling on
</VirtualHost>
</IfModule>
Do a configtest to check for errors.
apachectl -t
Reload if Syntax OK is displayed.
service apache2 reload
Access the website on IE (on Vista and above) or Firefox 26+ and check the error log.
tail /var/log/apache2/error.log
If the file defined in the SSLCACertificateFile directive is missing, a certificate an error similar to the following is displayed.
[Fri May 09 23:36:44.055900 2014] [ssl:error] [pid 1491:tid 139921007208320] AH02217: ssl_stapling_init_cert: Can't retrieve issuer certificate!
[Fri May 09 23:36:44.056018 2014] [ssl:error] [pid 1491:tid 139921007208320] AH02235: Unable to configure server certificate for stapling
If no such errors are displayed proceed to the final step.
Configuring OCSP stapling on Nginx
Edit the SSL virtual hosts file and place the following directives inside the server {} section.
sudo nano /etc/nginx/sites-enabled/example.com.ssl
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/ssl/private/ca-certs.pem;
If you followed this article to setup SSL hosts on Nginx the complete virtual host file will look like this:
/etc/nginx/sites-enabled/example.com.ssl
server {
listen 443;
server_name example.org;
root /usr/share/nginx/www;
index index.html index.htm;
ssl on;
ssl_certificate /etc/nginx/ssl/example.org/server.crt;
ssl_certificate_key /etc/nginx/ssl/example.org/server.key;
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate /etc/ssl/private/ca-certs.pem;
}
Do a configtest to see if everything is correct.
service nginx configtest
Then reload the nginx service.
service nginx reload
Access the website on IE (on Vista and above) or Firefox 26+ and check the error log.
tail /var/log/nginx/error.log
If the file defined in ssl_trusted_certificate is missing a certificate an error similar to the following is displayed:
2014/05/09 17:38:16 [error] 1580#0: OCSP_basic_verify() failed (SSL: error:27069065:OCSP routines:OCSP_basic_verify:certificate verify error:Verify error:unable to get local issuer certificate) while requesting certificate status, responder: ocsp.startssl.com
If no such errors are displayed proceed to the next step.
Testing OCSP Stapling
Two methods will be explained to test if OCSP stapling is working - the openssl command-line tool and SSL test at Qualys.
The OpenSSL command
This command’s output displays a section which says if your web server responded with OCSP data. We grep this particular section and display it.
echo QUIT | openssl s_client -connect www.digitalocean.com:443 -status 2> /dev/null | grep -A 17 'OCSP response:' | grep -B 17 'Next Update'
Replace www.digitalocean.com with your domain name. If OCSP stapling is working properly the following output is displayed.
OCSP response:
======================================
OCSP Response Data:
OCSP Response Status: successful (0x0)
Response Type: Basic OCSP Response
Version: 1 (0x0)
Responder Id: 4C58CB25F0414F52F428C881439BA6A8A0E692E5
Produced At: May 9 08:45:00 2014 GMT
Responses:
Certificate ID:
Hash Algorithm: sha1
Issuer Name Hash: B8A299F09D061DD5C1588F76CC89FF57092B94DD
Issuer Key Hash: 4C58CB25F0414F52F428C881439BA6A8A0E692E5
Serial Number: 0161FF00CCBFF6C07D2D3BB4D8340A23
Cert Status: good
This Update: May 9 08:45:00 2014 GMT
Next Update: May 16 09:00:00 2014 GMT
No output is displayed if OCSP stapling is not working.
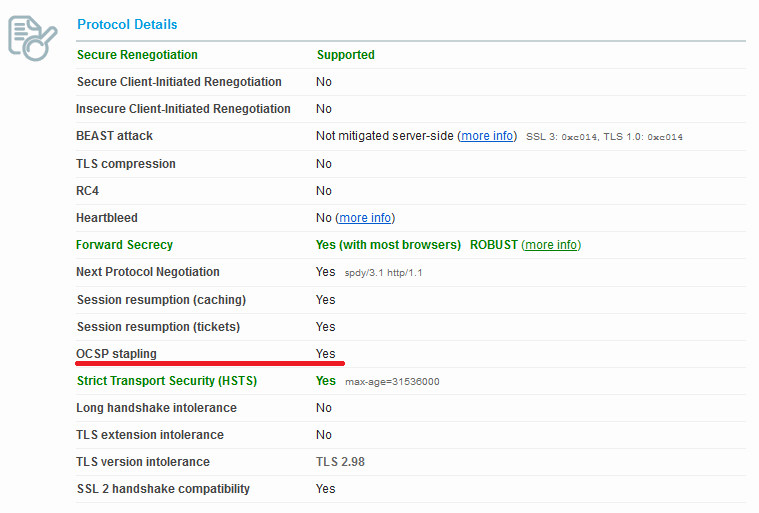
Qualys online SSL test
To check this online go to this website and enter your domain name. Once testing completes check under the Protocol Details section.
Additional reading
- Mozilla’s article on OCSP stapling - http://en.wikipedia.org/wiki/OCSP_stapling
- Wikipedia article on OCSP stapling - http://en.wikipedia.org/wiki/OCSP_stapling
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
Thanks guys, great guide! Just enabled OCSP stapling on my Nginx cluster.
One thing I noticed is that the command to test the OCSP response does not work correctly with servers that use SNI. For that, you must specify the -servername flag, e.g.:
Hi. I use Apache 2.4 and CloudFlare DNS and CloudFlare tls certificates. I have three certificate files:
I use private-key.key for SSLCertificateKeyFile I use intermediate.pem + root.pem for SSLCACertificateFile
Which certificate file should I use in SSLCertificateFile?
I wait for help. Thanks
Can OCSP Stapling be configured globally (Apache 2.4) by editing /etc/apache2/mods-available/ssl.conf
SSLUseStapling On SSLStaplingReturnResponderErrors off SSLStaplingResponderTimeout 5 SSLStaplingCache shmcb:${APACHE_RUN_DIR}/ssl_stapling_cache(128000)
I got
OCSP response:
OCSP Response Data: OCSP Response Status: successful (0x0) Response Type: Basic OCSP Response Version: 1 (0x0) Responder Id: 3DD350A5D6A0ADEEF34A600A65D321D4F8F8D60F Produced At: Mar 27 06:42:00 2016 GMT Responses: Certificate ID: Hash Algorithm: sha1 Issuer Name Hash: 49F4BD8A18BF760698C5DE402D683B716AE4E686 Issuer Key Hash: 3DD350A5D6A0ADEEF34A600A65D321D4F8F8D60F Serial Number: 0F53BC042737F712F3856510758DE162 Cert Status: good This Update: Mar 27 06:42:00 2016 GMT Next Update: Apr 3 05:57:00 2016 GMT
But the qualys test show OCSP not enabled. Why is that ?
Thank you for great article but i cant enable OCSP stapling although i’ve got A+ on ssllabs but when i see openssl status it gives me this
My .crt file in ssl_trusted_certificate has one server certificate, two intermediate and one root certi . (at least https://www.digicert.com/help/ shows that)
This comment has been deleted
Actual Retrieve the CA bundle for StartSSL
@jesin I checked the error.log and it is returning this message:
2015/06/19 14:37:41 [error] 21257#0: OCSP_basic_verify() failed (SSL: error:27069065:OCSP routines:OCSP_basic_verify:certificate verify error:Verify error:unable to get issuer certificate) while requesting certificate status, responder: gk.symcd.com
I downloaded the “Root 3” from this address https://www.geotrust.com/resources/root-certificates/ and I concatenated it with the .crt intermadiate certificate that CA sent to me by e-mail.
Is this the right certificate for use?
Thanks again!
By the way, this is my config file.
server { listen 80; server_name mysite.com; return 301 https://www.mysite.com$request_uri; }
server { listen 443 ssl spdy; keepalive_timeout 120; ssl on; ssl_certificate /etc/nginx/ssl/www.mysite.com.crt; ssl_certificate_key /etc/nginx/ssl/www_mysite_com.key; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers AES256+EECDH:AES256+EDH; ssl_dhparam /etc/nginx/ssl/dhparam.pem; ssl_session_cache shared:SSL:20m; ssl_session_timeout 20m; ssl_session_tickets on; ## ssl_stapling on; ## ssl_stapling_verify on; ## resolver 8.8.4.4 8.8.8.8 valid=300s; ## resolver_timeout 10s; ## ssl_trusted_certificate /etc/nginx/ssl/private/ca-certs.pem; add_header Strict-Transport-Security max-age=31536000; add_header X-Content-Type-Options nosniff; add_header X-Frame-Options DENY;
}
Hi @jesin, they provided only the intermediate certificate. The other one has my name. I followed a tutorial from here to convert these two files and install it in my server. Thanks for your response and support.
Hi Jesin, I’m using a Geotrust SSL-EV in my site. The certificate comes in .crt and .key extentions.
May you help me with the command line to retrieve the CA bundle from Geotrust and convert it to .pem?
Thank you very much in advance!