Tutorial
How To Install Squid Proxy on Ubuntu 12.10 x64

Not using Ubuntu 12.04?Choose a different version or distribution.
Step 1 - Spin up a Ubuntu 12.10 x64 droplet
Step 2 - Install Squid
apt-get install -y squid update-rc.d squid3 defaults
Step 3 - Setup Access Restrictions
Since this Squid proxy would allow anyone using it to make connections from your droplet's IP address, you would want to restrict access to it.
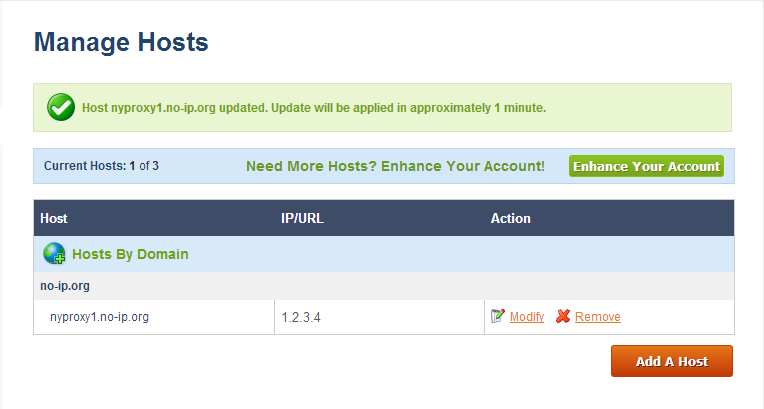
You can register a free dynamic IP from services like noip.com
If you would like to use this Squid proxy from your phone, you would have to install a dynamic DNS update client.
You can use applications like Dynamic DNS Client for Android, or FreeDynPro for iOS
.
Once you have a dynamic IP hostname, you can update it from your router at home, mobile device, or an API call.
This hostname should be added to /etc/squid3/squid.conf. Edit the file and add your hostname (nyproxy1.no-ip.org in our case):
acl myhost srcdomain nyproxy1.no-ip.org http_access allow myhost

Setup a crontab that reloads Squid every hour, in case your IP address changes:
echo 0 */1 * * * service squid3 reload >> /var/spool/cron/root
Step 4 - Configure Squid Proxy
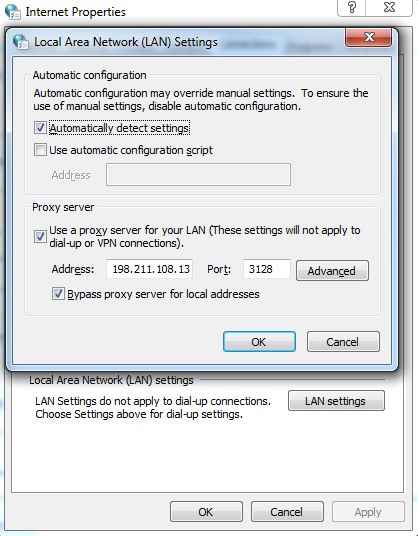
By default, Squid listens on port 3128. If you would like to use a different port, modify /etc/squid3/squid.conf
http_port 3128
If you would like to browse through this Squid proxy and not have it detected as a proxy, setup anonymous settings by adding these lines to /etc/squid3/squid.conf:
via off forwarded_for off request_header_access Allow allow all request_header_access Authorization allow all request_header_access WWW-Authenticate allow all request_header_access Proxy-Authorization allow all request_header_access Proxy-Authenticate allow all request_header_access Cache-Control allow all request_header_access Content-Encoding allow all request_header_access Content-Length allow all request_header_access Content-Type allow all request_header_access Date allow all request_header_access Expires allow all request_header_access Host allow all request_header_access If-Modified-Since allow all request_header_access Last-Modified allow all request_header_access Location allow all request_header_access Pragma allow all request_header_access Accept allow all request_header_access Accept-Charset allow all request_header_access Accept-Encoding allow all request_header_access Accept-Language allow all request_header_access Content-Language allow all request_header_access Mime-Version allow all request_header_access Retry-After allow all request_header_access Title allow all request_header_access Connection allow all request_header_access Proxy-Connection allow all request_header_access User-Agent allow all request_header_access Cookie allow all request_header_access All deny all
Step 5 - Start Squid proxy service
service squid3 start
Step 6 - Modify your browser's proxy settings
Step 7 - Verify Squid proxy works
Navigate over to whatismyip.com

And you are all done!
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
The following is an exact copy of my configuration for my anonymous squid3.3 proxy. I used some help from http://wiki.squid-cache.org/SquidFaq/ConfiguringSquid and appended the information I found in this article. After all was said and done this is the configuration that worked for me. Remember to place YOUR IP under acl myhost src instead of XX.XXX.XX.XXX (this is the ip you’re using to connect to the proxy server). The proxy server will only route traffic to this source address and all other ip addresses will not work; in this way the proxy is somewhat secure and only your ip address can use it. Good Luck :)
Can’t we setup a proxy with user names and passwords? Plus how can we determine how much bandwidth is used per account?
How to install 3proxy (small proxy) on digital ocean (ubuntu, debian): https://teamhelps.pp.ua/top/ustanovka-3proxy-na-digital-ocean-ubuntu-debian/
Except that this method (but with 16.04) doesn’t always works (even if I limit access to VPS by IP). Some sites just lie that IP is blocked because I run parsing bot on them (I didn’t).
The configuration is outdated and it’s wrong! If you’re pointing to your domain using
srcdomainthe squid is NOT convert your hostname to IP address. Change it fromacl myhost srcdomain nyproxy1.no-ip.orgtoacl myhost src nyproxy1.no-ip.organd it will work. Check out the wiki from the official site HEREAny updates for this? DO does not offer ubuntu 12.10 anymore.
enable the transparent option for interception caching
http_port 3128 transparent
#IP not Srcdomain acl myhost src x.x.x.x
Guys, change the default port and make sure there are login requirements or allowed IP’s - someone has been scanning a range of IP addresses and got mine, then used it to spam.
I got abuse reports for this.
make sure you dont have http_access deny all in your config file.otherwise proxy wont work
This comment has been deleted