- Log in to:
- Community
- DigitalOcean
- Sign up for:
- Community
- DigitalOcean
By Haley Mills
Not using CentOS 7?
Choose a different version or distribution.
Introduction
The Apache HTTP server is the most widely-used web server in the world. It provides many powerful features including dynamically loadable modules, robust media support, and extensive integration with other popular software.
In this guide, you will install an Apache web server with virtual hosts on your CentOS 7 server.
Prerequisites
You will need the following to complete this guide:
- A non-root user with sudo privileges configured on your server, set up by following the initial server setup guide for CentOS 7.
- A domain name configured to point to your server. You can learn how to point domains to DigitalOcean Droplets by following the How To Set Up a Host Name with DigitalOcean tutorial.
- A basic firewall configured by following the Additional Recommended Steps for New CentOS 7 Servers guide.
Step 1 — Installing Apache
Apache is available within CentOS’s default software repositories, which means you can install it with the yum package manager.
As the non-root sudo user configured in the prerequisites, update the local Apache httpd package index to reflect the latest upstream changes:
- sudo yum update httpd
Once the packages are updated, install the Apache package:
- sudo yum install httpd
After confirming the installation, yum will install Apache and all required dependencies.
If you completed the Additional Recommended Steps for New CentOS 7 Servers guide mentioned in the prerequisites section, you will have installed firewalld on your server and you’ll need to open up port 80 to allow Apache to serve requests over HTTP. If you haven’t already done so, you can do this by enabling firewalld’s http service with the following command:
- sudo firewall-cmd --permanent --add-service=http
If you plan to configure Apache to serve content over HTTPS, you will also want to open up port 443 by enabling the https service:
- sudo firewall-cmd --permanent --add-service=https
Next, reload the firewall to put these new rules into effect:
- sudo firewall-cmd --reload
After the firewall reloads, you are ready to start the service and check the web server.
Step 2 — Checking your Web Server
Apache does not automatically start on CentOS once the installation completes. You will need to start the Apache process manually:
- sudo systemctl start httpd
Verify that the service is running with the following command:
- sudo systemctl status httpd
You will see an active status when the service is running:
OutputRedirecting to /bin/systemctl status httpd.service
● httpd.service - The Apache HTTP Server
Loaded: loaded (/usr/lib/systemd/system/httpd.service; enabled; vendor preset: disabled)
Active: active (running) since Wed 2019-02-20 01:29:08 UTC; 5s ago
Docs: man:httpd(8)
man:apachectl(8)
Main PID: 1290 (httpd)
Status: "Processing requests..."
CGroup: /system.slice/httpd.service
├─1290 /usr/sbin/httpd -DFOREGROUND
├─1291 /usr/sbin/httpd -DFOREGROUND
├─1292 /usr/sbin/httpd -DFOREGROUND
├─1293 /usr/sbin/httpd -DFOREGROUND
├─1294 /usr/sbin/httpd -DFOREGROUND
└─1295 /usr/sbin/httpd -DFOREGROUND
...
As you can see from this output, the service appears to have started successfully. However, the best way to test this is to request a page from Apache.
You can access the default Apache landing page to confirm that the software is running properly through your IP address. If you do not know your server’s IP address, you can get it a few different ways from the command line.
Type this at your server’s command prompt:
- hostname -I
This command will display all of the host’s network addresses, so you will get back a few IP addresses separated by spaces. You can try each in your web browser to see if they work.
Alternatively, you can use curl to request your IP from icanhazip.com, which will give you your public IPv4 address as seen from another location on the internet:
- curl -4 icanhazip.com
When you have your server’s IP address, enter it into your browser’s address bar:
http://your_server_ip
You’ll see the default CentOS 7 Apache web page:
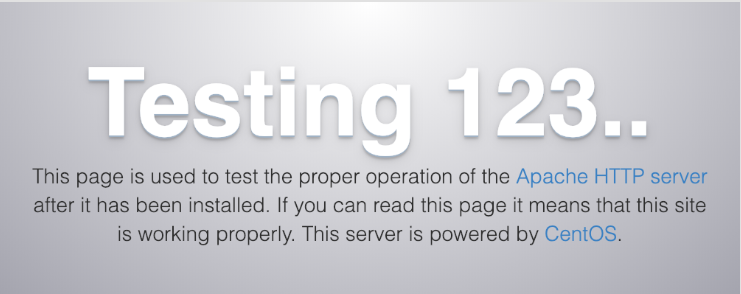
This page indicates that Apache is working correctly. It also includes some basic information about important Apache files and directory locations. Now that the service is installed and running, you can now use different systemctl commands to manage the service.
Step 3 — Managing the Apache Process
Now that you have your web server up and running, let’s go over some basic management commands.
To stop your web server, type:
- sudo systemctl stop httpd
To start the web server when it is stopped, type:
- sudo systemctl start httpd
To stop and then start the service again, type:
- sudo systemctl restart httpd
If you are simply making configuration changes, Apache can often reload without dropping connections. To do this, use this command:
- sudo systemctl reload httpd
By default, Apache is configured to start automatically when the server boots. If this is not what you want, disable this behavior by typing:
- sudo systemctl disable httpd
To re-enable the service to start up at boot, type:
- sudo systemctl enable httpd
Apache will now start automatically when the server boots again.
The default configuration for Apache will allow your server to host a single website. If you plan on hosting multiple domains on your server, you will need to configure virtual hosts on your Apache web server.
Step 4 — Setting Up Virtual Hosts (Recommended)
When using the Apache web server, you can use virtual hosts (similar to server blocks in Nginx) to encapsulate configuration details and host more than one domain from a single server. In this step, you will set up a domain that is referred to as your_domain, but you should replace this with your own domain name. To learn more about setting up a domain name with DigitalOcean, see our Introduction to DigitalOcean DNS.
Apache on CentOS 7 has one server block enabled by default that is configured to serve documents from the /var/www/html directory. While this works well for a single site, it can become unwieldy if you are hosting multiple sites. Instead of modifying /var/www/html, you will create a directory structure within /var/www for the your_domain site, leaving /var/www/html in place as the default directory to be served if a client request doesn’t match any other sites.
Create the html directory for your_domain as follows, using the -p flag to create any necessary parent directories:
- sudo mkdir -p /var/www/your_domain/html
Create an additional directory to store log files for the site:
- sudo mkdir -p /var/www/your_domain/log
Next, assign ownership of the html directory with the $USER environmental variable:
- sudo chown -R $USER:$USER /var/www/your_domain/html
Make sure that your web root has the default permissions set:
- sudo chmod -R 755 /var/www
Next, create a sample index.html page using vi or your favorite editor:
- sudo vi /var/www/your_domain/html/index.html
Press i to switch to INSERT mode and add the following sample HTML to the file:
<html>
<head>
<title>Welcome to your website!</title>
</head>
<body>
<h1>Success! The your_domain virtual host is working!</h1>
</body>
</html>
Save and close the file by pressing ESC, typing :wq, and pressing ENTER.
With your site directory and sample index file in place, you are almost ready to create the virtual host files. Virtual host files specify the configuration of your separate sites and tell the Apache web server how to respond to various domain requests.
Before you create your virtual hosts, you will need to create a sites-available directory to store them in. You will also create the sites-enabled directory that tells Apache that a virtual host is ready to serve to visitors. The sites-enabled directory will hold symbolic links to virtual hosts that we want to publish. Create both directories with the following command:
- sudo mkdir /etc/httpd/sites-available /etc/httpd/sites-enabled
Next, you will tell Apache to look for virtual hosts in the sites-enabled directory. To accomplish this, edit Apache’s main configuration file and add a line declaring an optional directory for additional configuration files:
- sudo vi /etc/httpd/conf/httpd.conf
Add this line to the end of the file:
IncludeOptional sites-enabled/*.conf
Save and close the file when you are done adding that line. Now that you have your virtual host directories in place, you will create your virtual host file.
Start by creating a new file in the sites-available directory:
- sudo vi /etc/httpd/sites-available/your_domain.conf
Add in the following configuration block, and change the your_domain domain to your domain name:
<VirtualHost *:80>
ServerName www.your_domain
ServerAlias your_domain
DocumentRoot /var/www/your_domain/html
ErrorLog /var/www/your_domain/log/error.log
CustomLog /var/www/your_domain/log/requests.log combined
</VirtualHost>
This will tell Apache where to find the root directly that holds the publicly accessible web documents. It also tells Apache where to store error and request logs for this particular site.
Save and close the file when you are finished.
Now that you have created the virtual host files, you will enable them so that Apache knows to serve them to visitors. To do this, create a symbolic link for each virtual host in the sites-enabled directory:
- sudo ln -s /etc/httpd/sites-available/your_domain.conf /etc/httpd/sites-enabled/your_domain.conf
Your virtual host is now configured and ready to serve content. Before restarting the Apache service, let’s make sure that SELinux has the correct policies in place for your virtual hosts.
Step 5 — Adjusting SELinux Permissions for Virtual Hosts (Recommended)
SELinux is configured to work with the default Apache configuration. Since you set up a custom log directory in the virtual hosts configuration file, you will receive an error if you attempt to start the Apache service. To resolve this, you need to update the SELinux policies to allow Apache to write to the necessary files. SELinux brings heightened security to your CentOS 7 environment, therefore it is not recommended to completely disable the kernel module.
There are different ways to set policies based on your environment’s needs, as SELinux allows you to customize your security level. This step will cover two methods of adjusting Apache policies: universally and on a specific directory. Adjusting policies on directories is more secure, and is therefore the recommended approach.
Adjusting Apache Policies Universally
Setting the Apache policy universally will tell SELinux to treat all Apache processes identically by using the httpd_unified boolean. While this approach is more convenient, it will not give you the same level of control as an approach that focuses on a file or directory policy.
Run the following command to set a universal Apache policy:
- sudo setsebool -P httpd_unified 1
The setsebool command changes SELinux boolean values. The -P flag will update the boot-time value, making this change persist across reboots. httpd_unified is the boolean that will tell SELinux to treat all Apache processes as the same type, so you enabled it with a value of 1.
Adjusting Apache Policies on a Directory
Individually setting SELinux permissions for the /var/www/your_domain/log directory will give you more control over your Apache policies, but may also require more maintenance. Since this option is not universally setting policies, you will need to manually set the context type for any new log directories specified in your virtual host configurations.
First, check the context type that SELinux gave the /var/www/your_domain/log directory:
- sudo ls -dZ /var/www/your_domain/log/
This command lists and prints the SELinux context of the directory. You will see output similar to the following:
Outputdrwxr-xr-x. root root unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/your_domain/log/
The current context is httpd_sys_content_t, which tells SELinux that the Apache process can only read files created in this directory. In this tutorial, you will change the context type of the /var/www/your_domain/log directory to httpd_log_t. This type will allow Apache to generate and append to web application log files:
- sudo semanage fcontext -a -t httpd_log_t "/var/www/your_domain/log(/.*)?"
Next, use the restorecon command to apply these changes and have them persist across reboots:
- sudo restorecon -R -v /var/www/your_domain/log
The -R flag runs this command recursively, meaning it will update any existing files to use the new context. The -v flag will print the context changes the command made. You will see the following output confirming the changes:
Outputrestorecon reset /var/www/your_domain/log context unconfined_u:object_r:httpd_sys_content_t:s0->unconfined_u:object_r:httpd_log_t:s0
You can list the contexts once more to see the changes:
- sudo ls -dZ /var/www/your_domain/log/
The output reflects the updated context type:
Outputdrwxr-xr-x. root root unconfined_u:object_r:httpd_log_t:s0 /var/www/your_domain/log
Now that the /var/www/your_domain/log directory is using the httpd_log_t type, you are ready to test your virtual host configuration.
Step 6 — Testing the Virtual Host (Recommended)
Once the SELinux context has been updated with either method, Apache will be able to write to the /var/www/your_domain/log directory. You can now successfully restart the Apache service:
- sudo systemctl restart httpd
List the contents of the /var/www/your_domain/log directory to see if Apache created the log files:
- ls -lZ /var/www/your_domain/log
You’ll see that Apache was able to create the error.log and requests.log files specified in the virtual host configuration:
Output-rw-r--r--. 1 root root 0 Feb 26 22:54 error.log
-rw-r--r--. 1 root root 0 Feb 26 22:54 requests.log
Now that you have your virtual host set up and SELinux permissions updated, Apache will now serve your domain name. You can test this by navigating to http://your_domain, where you should see something like this:
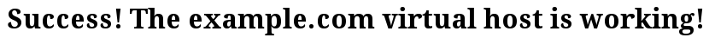
This confirms that your virtual host is successfully configured and serving content. Repeat Steps 4 and 5 to create new virtual hosts with SELinux permissions for additional domains.
Conclusion
In this tutorial, you installed and managed the Apache web server. Now that you have your web server installed, you have many options for the type of content you can serve and the technologies you can use to create a richer experience.
If you’d like to build out a more complete application stack, you can look at this article on how to configure a LAMP stack on CentOS 7.
Thanks for learning with the DigitalOcean Community. Check out our offerings for compute, storage, networking, and managed databases.
About the author
Still looking for an answer?
This textbox defaults to using Markdown to format your answer.
You can type !ref in this text area to quickly search our full set of tutorials, documentation & marketplace offerings and insert the link!
Great stuff, but 2 things happened…
- When I did a http://192.168.56.109 on my Windows PC before, it went to the Testing …1…2…3 site, but after I followed your procedure, it now goes to my virtual site, and I cannot get to the Testing …1…2…3 anymore.
- http://example.com only work from the vitrual server on which I created this virtual host, when I try it from my Windows PC, I just get a <This site can’t be reached> in my browser.
Does it mean I have to fix (1) by adding the default directory as another virtual server? But how do I fix (2)?
Thanks in advance.
James
This comment has been deleted
It’s counter-intuitive to include “sudo” in any of the commands in this (and any other digital ocean) tutorial(s). If I/we have access to install/start/stop apache or edit vhosts, I don’t need to use sudo.
I have been setting up Linux web servers since the late 1990’s I have tried all of the different methods through RedHat based Linuxes. I have always embraced SELinux, though I have cursed it many times.
This tutorial led me for the first time to create and use the enabled sites directory and stay out of the default Apache directory. since I am setting up a development server at this time I liked using the “setsebool -P httpd_unified 1” command. This command was the big deal for me in this tutorial.
Thanks for your efforts, you did a great job.
I also had to run
sudo firewall-cmd --add-service=http
sudo firewall-cmd --add-service=https
I’ve followed all of your instructions just changed servername to www.webserver.com. But face the problem after test this by navigating to http://webserver.com >> “Server not found”. But when I try to navigate it to server’s IP http://ip_server >> display “/var/www/example.com/html/index.html”. Success! The example.com…
After I had run this command “sudo systemctl restart httpd”, I got this and I have been battling it: “Job for httpd.service failed because the control process exited with error code. See “systemctl status httpd.service” and “journalctl -xe” for details.”
I don’t need to change the log folder to httpd_log_t as it seems it’s already writing to log files while having httpd_sys_content_t as the SELinux context.
This is my current ls -dZ output:
drwxr-xr-x. apache apache unconfined_u:object_r:httpd_sys_content_t:s0 /var/www/cbdhempoilusa.com/log
On the other hand, for another virtual host, I’ve set this as you explained in this tutorial but like I’ve said - there is no visible difference.
Using Centos 7 and having apache:apache as the ownership of the files
- Table of contents
- Prerequisites
- Step 1 — Installing Apache
- Step 2 — Checking your Web Server
- Step 3 — Managing the Apache Process
- Step 4 — Setting Up Virtual Hosts (Recommended)
- Step 5 — Adjusting SELinux Permissions for Virtual Hosts (Recommended)
- Step 6 — Testing the Virtual Host (Recommended)
- Conclusion
Deploy on DigitalOcean
Click below to sign up for DigitalOcean's virtual machines, Databases, and AIML products.
Become a contributor for community
Get paid to write technical tutorials and select a tech-focused charity to receive a matching donation.
DigitalOcean Documentation
Full documentation for every DigitalOcean product.
Resources for startups and SMBs
The Wave has everything you need to know about building a business, from raising funding to marketing your product.
Get our newsletter
Stay up to date by signing up for DigitalOcean’s Infrastructure as a Newsletter.
New accounts only. By submitting your email you agree to our Privacy Policy
The developer cloud
Scale up as you grow — whether you're running one virtual machine or ten thousand.
Get started for free
Sign up and get $200 in credit for your first 60 days with DigitalOcean.*
*This promotional offer applies to new accounts only.
